Protecting credit card numbers used in online transactions is the most often-cited example of the need for web security. So let’s look at the typical credit card transactions, observe what the risks are, and see how web security makes a difference.
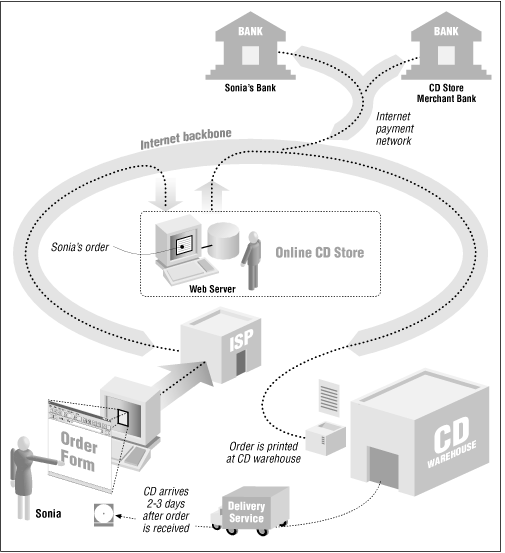
Consider a typical transaction on the Web: buying a CD from an online music store with your credit card (Figure 1.1).
In this example, a teenager—call her Sonia—sits down at her dad’s computer, finds a music store on the World Wide Web, and browses the company’s catalog. Sonia finds a rare compact disc that she has been looking for desperately—say, a collection of Led Zeppelin songs as performed by Tiny Tim. She creates an order with the store’s electronic shopping cart, types in her name and shipping address, types in her dad’s credit card number, and clicks an onscreen button in her web browser display labeled BUY-IT. Sonia’s CD arrives in the mail soon thereafter. A month later, her dad gets the credit card bill in the mail. He and Sonia then have a little discussion about her allowance and the fact that she isn’t doing enough chores around the house.
Both the credit card holder (Sonia’s dad) and the merchant face risks in this transaction. For the credit card holder, two risks are obvious and well-publicized:
The credit card number might be “sniffed” by some electronic villain as it travels across the Internet. That person could then use the credit card number to commit fraud. To make things worse, the credit card holder might not realize the card’s number has been stolen until the statement is received. By that point, the card’s credit limit has probably been maxed out with many thousands of dollars in fraudulent charges. Let’s hope this doesn’t happen while Dad is on a business trip.
The credit card might get billed, but the CD might never show up. When Sonia tries to investigate, she finds that there is no electronic CD store: the whole thing was a scam, and Sonia has lost her dad’s money. The company that billed the credit card doesn’t even exist anymore.
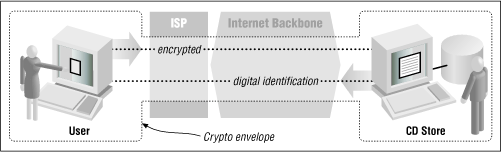
It’s these two risks that Netscape’s SSL was designed to combat. SSL uses encryption, a mathematical technique for scrambling information, so that data sent between Sonia’s web browser and the online music store can’t be surreptitiously monitored while it is in transit (see Figure 1.2). SSL also supports a sophisticated system for digital identification, so that Sonia has some assurance that the people operating the online music store are really who they claim to be. (Encryption is described in Chapter 10, and digital IDs are described in Chapter 6.)
SSL does a good job of protecting information while the data is in transit and giving web users good assurances that they are communicating with the sites they think they are. Programs that implement the SSL protocol come in two versions: a reduced-strength version that is sold by U.S. corporations overseas, and a full-strength version sold by foreign companies overseas as well as by U.S. companies for use within the United States. But even though a lot of fuss has been made because the reduced-strength version of the SSL program isn’t all that secure, it is still probably good enough for encrypting most credit card transactions.[6]
Nevertheless, it’s ironic that SSL was first proposed as a safe way for sending credit card numbers over the Internet, because it wasn’t needed for this purpose. Here’s why:
According to the laws that govern the use of credit cards in the United States, consumers are only liable for the first $50 of fraudulent credit card transactions. In most cases, credit card companies don’t even enforce the $50 limit—consumers who report fraudulent charges can simply alert their banks and not pay. So there really isn’t any risk to consumers in having their credit card numbers “sniffed” over the Internet.[7]
If Sonia were billed for a CD and it never showed up, all her dad would have to do is write his credit card company to contest the charge.[8]
There is no need for consumers to verify the identity of merchants that accept credit cards, because the banks that issue merchants their credit card accounts have already done this for the consumer. Merchants can’t charge your credit card unless they first obtain a credit card merchant account, which involves an extensive application procedure, a background check, and usually an onsite visit. Indeed, credit card firms do a far better job of this verification than Sonia could ever hope to do by herself.
The idea that SSL could secure credit card transactions was an important part of selling Internet commerce—and specifically Netscape’s products—to consumers. The message was simple and effective: “Don’t do business with companies that don’t have secure (i.e., Netscape) web servers.” But the message was too effective: many Internet users, including some journalists, were so intimidated by the idea of having their credit card information stolen on the Internet that they refused to do business with merchants that had cryptographic web servers as well.
Ironically, the people who were really protected by Netscape’s technology weren’t the consumers, but banks and merchants. That’s because they are the ones who are ultimately responsible for credit card fraud. If a credit card merchant gets a credit card approved and ships out a CD, the bank is obligated to pay the merchant for the charge, even if the credit card is reported stolen later that day. The encryption also protects merchants: if a credit card number is stolen because of a merchant’s negligence, then the merchant can be held liable by the bank for any fraud committed on the card. (Credit card companies have since stated that merchants are indeed responsible for any fraud that results from credit card numbers that are stolen if a merchant didn’t use a cryptographically enabled web server. Nevertheless, at this point there has been no publicly reported example of a credit card number being “sniffed” over a network connection, encrypted or not.)
The American Bankers Association maintains that it’s in the interest of consumers to protect banks and merchants from fraud. After all, fraud cuts into the profits of banks, forcing them to raise interest rates and making it harder for them to offer new services. Dealing with fraud can also be very difficult for some consumers. Some people panic when faced with a credit card bill that contains thousands of dollars in fraudulent charges. Others simply ignore it. Unfortunately, they do so at their peril: after a period of time (depending on the financial institution), consumers become liable for fraudulent charges that are not contested.
It turns out that both Sonia and the merchant face many other risks when doing business over the Internet—risks that encryption really does not protect against. For Sonia, these risks include:
The risk that the information she provides for this transaction will be used against her at some time in the future. For instance, personal information may be obtained by a con artist and used to gain Sonia’s trust. Or the address that she gives may end up on a mailing list and used to bombard Sonia with unwanted physical or electronic mail.
The risk that the merchant may experiment with Sonia’s sensitivity to price or determine the other stores at which Sonia is shopping, allowing the merchant to selectively raise the prices that are offered to Sonia so that they will be as high as she is willing (or able) to pay—and definitely higher than the prices that are charged the “average” consumer.
The risk that the merchant might somehow take over Sonia’s web browser and use it to surreptitiously glean information from her computer about her tastes and desires.
The risk that a rogue computer programmer might figure out a way to gain control of Sonia’s web browser. That browser could then be used to reformat Sonia’s hard disk. Even worse: the rogue program might download a piece of software that scans Sonia’s computer for sensitive information (bank account numbers, credit card numbers, access codes, Social Security Numbers, and so on) and then silently upload that information to other sites on the Internet for future exploitation.
Likewise, the merchant faces real risks as well:
Sonia might try to click into the merchant’s web site and find it down or terribly sluggish. Discouraged, she buys the records from a competitor. Even worse, she then posts her complaints to mailing lists, newsgroups, and her own set of WWW pages.
Sonia might in fact be a competitor—or, actually, a robot from a competing web site—that is systematically scanning the music store’s inventory and obtaining a complete price list.
Sonia might be Jason, a 14-year-old computer prankster who has stolen Sonia’s credit card number and is using it illegally to improve his CD collection.
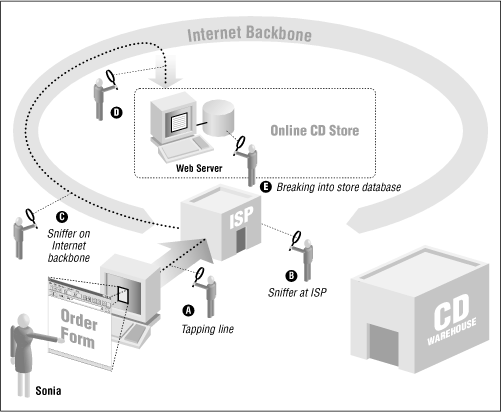
Once the merchant obtains Sonia’s credit card number, it is stored on the hard disk of the merchant’s computer. Jason might break into the computer and steal all the credit card numbers, opening the merchant to liability.
Once Jason breaks into the merchant’s computer, he might introduce fraudulent orders directly into the company’s order-processing database. A few days later, Jason receives thousands of CDs in the mail.
Jason might have his own credit card. Having thoroughly compromised the merchant’s computer, Jason begins inserting reverse charge orders into the merchant’s credit card processing system. The credits appear on Jason’s credit card. A few days later, he uses a neighborhood ATM machine to turn the credits into cash.
As a prank, or as revenge for some imagined slight, Jason might alter the store’s database or WWW pages so that the CDs customers receive are not the ones they ordered. This might not be discovered for a week or two, after thousands of orders have been placed. The merchant would have the expense of paying for all the returned CDs, processing the refunds, and losing the customer’s faith.
Or Jason might simply sabotage the online store by lowering the prices of the merchandise to below the store’s cost.
These are the real threats of doing business on the Internet. Some of them are shown in Figure 1.3.
There is nothing that is fundamentally new about these kinds of risks: they have existed for as long as people have done business by computer; some of these problems can also be experienced doing business by telephone or by mail. But the Internet and the World Wide Web magnify the risks substantially. One of the reasons for the heightened threat on today’s networks is that the Internet makes it far easier for people to wage anonymous or nearly anonymous attacks against users and businesses. These attacks, in turn, can be automated, which makes it possible for an attacker to scan thousands of web sites and millions of users for any given vulnerability within a very short amount of time. Finally, these attacks can be conducted worldwide, an unfortunate consequence of the Internet’s trans-national nature.
[6] Weak encryption is good enough for most credit card transactions because these transactions are reversible and heavily audited. Fraud is quickly discovered. And while it is true that an SSL transaction that’s encrypted with a 40-bit key can be cracked in a matter of hours by a graduate student with a laboratory of workstations, there is no easy way to tell before attempting to crack a message if it is a message worth cracking. It’s far, far easier to simply scan the Net for unencrypted credit card numbers.
[7] However, note that debit cards, which are being widely promoted by banks nowadays, may not have a customer liability limit. If you use a debit card, be sure to check the fine print in the agreement with your bank!
[8] Under the law, he would need to write the credit card company to preserve his rights to contest the charge—a telephone call is not sufficient, although the company might issue a temporary credit based on the call.
Get Web Security and Commerce now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.