8.4 The Tactical Edge
The GIG architecture calls for the HAIPE-based encryption to be the common architecture of the tactical theatre. One important reason for HAIPE encryption is to ensure that every IP packet that goes over the air is securely encrypted. This level of encryption ensures that enemy technology that sniffs packets from over the air, will fail to get any useful information, since HAIPE encryption is the most complex known encryption technique.
8.4.1 Tactical Edge Definition
The diverse possibilities of how the plain text IP layer can exist over the HAIPE encrypted core network, with the GIG architecture, creates what we will refer to as the tactical edge. The tactical edge, in this book, refers to the access points to the HAIPE encrypted network core and specifically the plain text IP layer access points as shown in Figure 8.3.
Figure 8.3 The tactical edge as the plain text IP layer access point to the GIG encrypted core.
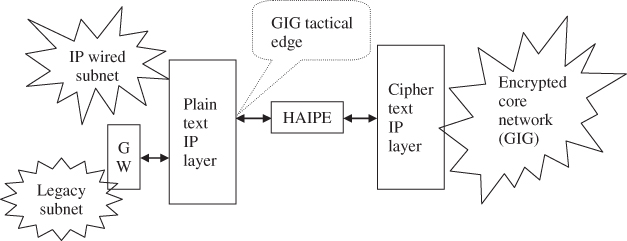
In Figure 8.3, there could be many users (with their applications, sessions, and transport layers) within the IP wired subnet. Also, the gateway (referred to in Figure 8.3 as “GW”), between the legacy non-IP subnet and the plain text IP layer, can map each legacy node to an IP address. This creates many IP instantiations that access the GIG core through the tactical edge point. Since HAIPE has a single plain text port, one will have a single plain ...
Get Tactical Wireless Communications and Networks: Design Concepts and Challenges now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

