Chapter 7. Vulnerability Management
“The weakest link in a chain is the strongest because it can break it.”—Stanislaw Jerzy Lec
Attackers need to exploit just one vulnerable system to gain access to your network. Once inside, they can establish multiple doorways to the outside, making it extremely difficult to completely remediate the breach. This is known as establishing a foothold according to Mandiant’s Targeted Attack Lifecycle.1 From there, the attacker can move about the network, causing havoc through internal attack campaigns, stealing data, and so on. Figure 7-1 shows the targeted attack lifecycle.
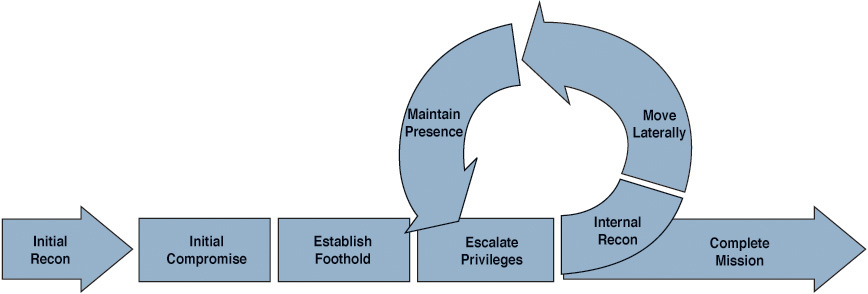
Figure 7-1 Targeted Attack Lifecycle ...
Get Security Operations Center: Building, Operating and Maintaining your SOC now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

