System Monitoring for Blanco Wireless
Blanco Wireless has configured targeted monitoring for its account management system. To monitor the system, Blanco is leveraging the following event sources:
NetFlow collection at the data center and DMZ gateways
Syslog collection from servers
NIDS
Database event logs from the Oracle 10g databases
Using Nagios, Blanco can automate system monitoring to ensure high availability for security monitoring (see Figure 7-5).
Note
Nagios setup and configuration is detailed on the Nagios website at http://www.nagios.org/. Plug-ins and scripts are listed at http://www.NagiosExchange.org/ and http://www.NagiosPlugins.org/.
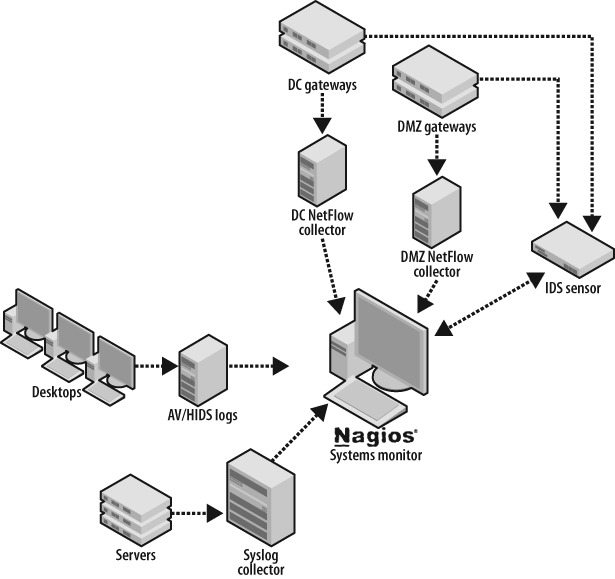
Figure 7-5. Automating system monitoring using Nagios to script checks for system health and continuous event flow
Monitor NetFlow Collection
The NetFlow collectors for Blanco are running OSU flow-tools for collecting and querying NetFlow records. To ensure continuous flow collection from critical sources (the DC and DMZ gateway routers sending flows to the collectors), Nagios plug-ins are configured to observe the following:
Collectors are continuously receiving flows from both data center and DMZ routers.
Collectors are in good health, so they’re able to receive and store flows properly.
Collection processes are running and functioning properly.
For Nagios to monitor the collectors, Blanco has deployed the NRPE daemon to run directly on the collectors. ...
Get Security Monitoring now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

