NetFlow
As we’ve asserted throughout this book, NetFlow is a free and powerful tool, and should be one of the most powerful tools in your security tool belt. NetFlow deployment is fairly simple. If you have a large enterprise, aggregating your data and performing queries across data sets can add complexity, but it can be scripted with some simple Perl. NetFlow is an invaluable forensic investigation tool that you can query on demand. The examples that follow are built on OSU flow-tools, which we discussed in Chapter 3.
Figure 6-13 depicts a simple
NetFlow collection in a small network environment. Notice that for ease of
operation and separation of data, we’re running two flow-capture instances on a single NetFlow
collector. The ISP gateway router is configured to export flows to the
collector on UDP port 2090 and the data center gateways are configured to
export on UDP 2095. The collector has one process listening on UDP 2090
for ISP gateway flows, and the other is listening for the DC gateway
flows.
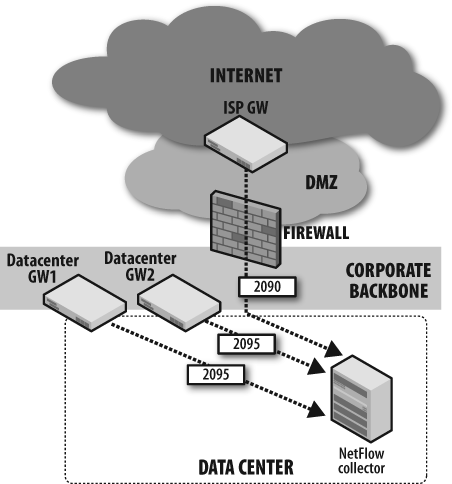
Figure 6-13. Simple NetFlow collection
This flow-capture command:
/usr/local/netflow/bin/flow-capture -w /var/local/flows/isp-data -E90G -V5 -A1134 0/0/2090 -S5 -p /var/run/netflow/isp-flow-capture.pid -N-1 -n288
contains several command-line flags, which will do the following:
Capture ISP gateway flows to the /var/local/flows/isp-data directory (make sure the NetFlow user can write here!) ...
Get Security Monitoring now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

