Step 4: Design a Secure Architecture
You should use a distributed architecture design, putting key components on separate computers. This builds in protection against any single point of failure. For example, Figure 13-1 takes a first stab at a secure architecture for a Web application that serves pages using http and https.
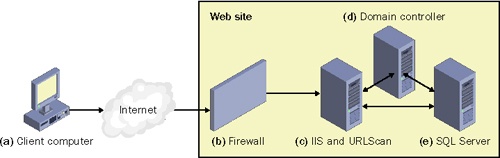
Figure 13-1. Secure Web application architecture 1
The client computer (a) browses through the Internet to the Web site. When the user’s computer sends a request to the Web site, it first encounters a firewall that blocks all communications except those on ports 80 (http) and 443 (https). After the firewall, the only computer ...
Get Security for Microsoft® Visual Basic® .NET now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

