Threat Assessment and the Threat Management Lifecycle
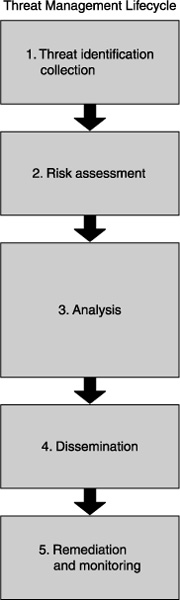
The threat assessment process, which is illustrated in Figure 4-1, should provide you with a methodology for identifying threats, determining their potential impact, and identifying which steps you need to take to mitigate the risk. It’s important to note that social media threats are still evolving, so determining their real impact on corporations is hard. With more data in another year or two, we can probably better quantify the effects. These next sections cover the basic structure of the threat assessment process and introduce the Threat Management Lifecycle.
Identify and Assess
Identify ...
Get Securing the Clicks Network Security in the Age of Social Media now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

