OAuth 2 Workflow
Warning
While the OAuth 2 specification drafts are clear about the parameters that are required in the exchange requests and responses at each stage, implementers may have slight discrepancies in the parameter lists that they support, even going so far as to not request or provide required parameters or to change the expected values for given parameters. Be aware of the fields that are required and the responses provided by any service that you are using. You can find this information in the OAuth implementation docs for each service.
The OAuth 2 workflow is a rather simple set of back-and-forth requests between a client and the provider site. The user is still involved in the process to authorize the application to access his privileged information, but in general the interaction is between the client and provider, which exchange simple verification resources in order to issue (provider) and obtain (client) a final access token to make privileged requests. This entire flow is illustrated in Figure 9-10.
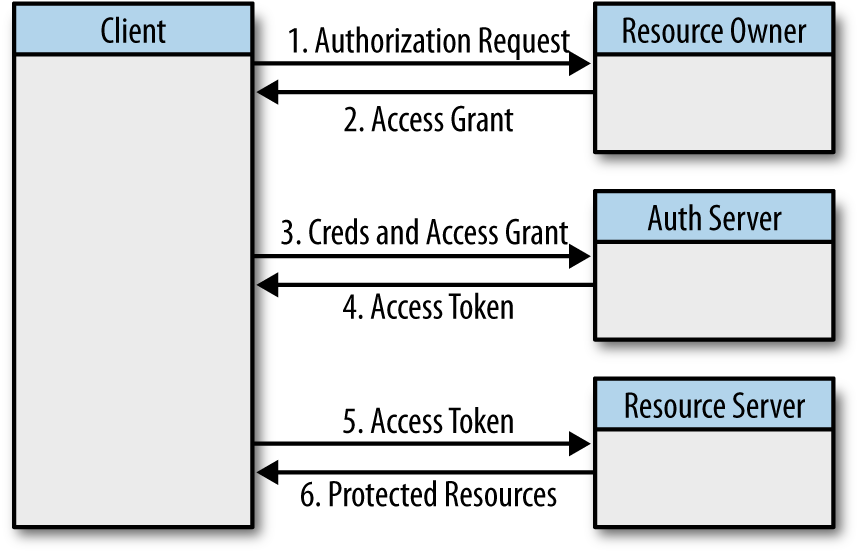
Figure 9-10. OAuth 2 authorization workflow
The OAuth 2 authorization flow consists of a few exchange requests. The flow depicted in Figure 9-10 contains the back-and-forth requests for obtaining the access token for a user and then making a request back to the provider’s resource server to obtain some protected data.
In short, the OAuth 2 authorization flow consists of ...
Get Programming Social Applications now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

