VMware Artifacts
The VMware environment leaves many artifacts on the system, especially when VMware Tools is installed. Malware can use these artifacts, which are present in the filesystem, registry, and process listing, to detect VMware.
For example, Figure 17-1 shows the process
listing for a standard VMware image with VMware Tools installed. Notice that three VMware processes
are running: VMwareService.exe, VMwareTray.exe, and
VMwareUser.exe. Any one of these can be found by malware as it searches the
process listing for the VMware string.
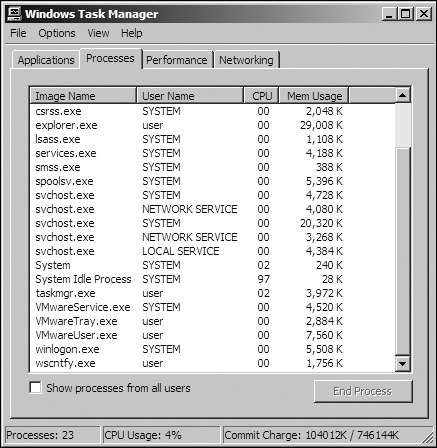
Figure 17-1. Process listing on a VMware image with VMware Tools running
VMwareService.exe runs the VMware ...
Get Practical Malware Analysis now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

