16.1 INTRODUCTION
In an ad hoc network, all the nodes may not be within the transmission range of each other; hence, nodes are often required to forward network traffic on behalf of other nodes. Consider for example the scenario in Figure 16.1, if node S sends data to node D, which is three hops away, the data traffic will get to its destination only of A and B forward it. The process of forwarding network traffic from source to destination is termed routing.
Secure routing in mobile ad hoc networks (MANETs) has emerged as an important MANET research area. MANETs, by virtue of the fact that they are wireless networks, are more vulnerable to intrusion by malicious agents than wired networks. In wired networks, appropriate physical security measures, such as restriction of physical access to network infrastructures, can be used to attenuate the risk of intrusions. Physical security measures are less effective, however, in limiting access to wireless network media. Consequently, MANETs are much more susceptible to infiltration by malicious agents. Authentication mechanisms can help to prevent unauthorized access to MANETs. However, considering the high likelihood that nodes with proper authentication credentials can be taken over by malicious entities, there are needs for security protocols that allow MANET nodes to operate in potential adversarial environments.
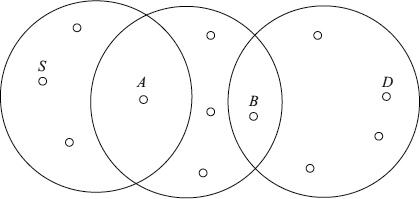
Figure 16.1 Multihop ...
Get Mobile Intelligence now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

