Security and Roles
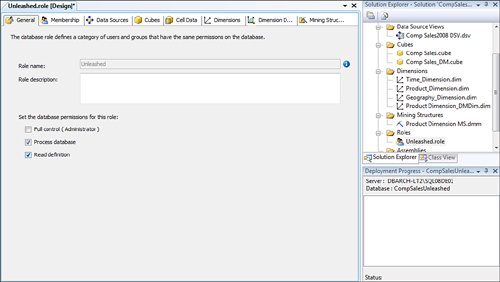
Security is straightforward in SSAS. For each database or cube, roles are identified with varying levels of granularity for users. Roles are used when accessing the data in cubes. The process works like this: a role is defined, and then an individual user or group who is a member of that role is assigned that role. To create the roles you need for this data, you right-click on the Roles entry in the Solution Explorer and select New Role. Figure 51.71 shows the creation of a database role with process database and read definition permissions.
Figure 51.71 Creating a database role and permissions in the role designer.
The other ...
Get Microsoft® SQL Server 2008 R2 Unleashed now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

