Up to this point, I’ve treated the Windows Server 2003 DNS service as a traditional nameserver, mostly compliant with the relevant RFCs, which can act in both primary and secondary “modes” for a zone. However, Windows Server 2003 offers a third mode specific to Windows that, although not listed in an RFC, offers some distinct advantages if you’ve made an infrastructure investment in Active Directory and Windows.
The third mode, Active Directory-integrated DNS, offers two plusses over traditional zones. For one, the fault tolerance built into Active Directory eliminates the need for primary and secondary nameservers. Effectively, all nameservers using Active Directory-integrated zones are primary nameservers. This has a huge advantage for the use of dynamic DNS as well: namely, the wide availability of nameservers that can accept registrations. Recall that domain controllers and workstations register their locations and availability to the DNS zone using dynamic DNS. In a traditional DNS setup, only one type of nameserver can accept these registrations—the primary server because it has the only read/write copy of a zone. By creating an Active Directory-integrated zone, all Windows Server 2003 nameservers that store that zone in Active Directory can accept a dynamic registration, and the change will be propagated using Active Directory multi-master replication. All you need to do to set up this scenario is install Windows Server 2003 on a machine, configure it as a domain controller, install the DNS service, and set up the zone. It’s all automatic after that. Contrast this with the standard primary-secondary nameserver setup, where the primary server is likely to be very busy handling requests and zone transfers without worrying about the added load of dynamic DNS registrations. Active Directory-integrated zones relieve this load considerably. And to add to the benefits, Active Directory-integrated zones support compression of replication traffic between sites, which also makes it unnecessary to use the old-style “uncompressed” zone transfers.
Tip
As you read in the previous section, part of the dynamic DNS functionality provided in Windows Server 2003 is the scavenger process. Recall the no-refresh interval function, which was created to eliminate exorbitant amounts of traffic being passed between domain controllers for each DNS reregistration.
Active Directory-integrated zones also afford a big security advantage, in that they provide the capability to lock down dynamic DNS functionality by restricting the ability of users and computers to register records into the system—only computers that are members of the Active Directory domain that hosts the DNS records can add and update records dynamically to these zones. However, to have an Active Directory-integrated zone, your nameservers must be domain controllers for an Active Directory domain. If other nameservers are used that are not domain controllers, they can act as only traditional secondary nameservers, holding a read-only copy of the zone and replicating via the traditional zone transfer process.
If you’re already running a nameserver that is a domain controller with an active zone in service, it’s easy to convert that to an Active Directory-integrated zone. (And for that matter, it’s easy to revert to a primary or secondary zone—this isn’t a be-all and end-all.) Here’s how to go forward:
Open the DNS Management snap-in.
Right-click the zone folder you want to convert, and select Properties from the context menu.
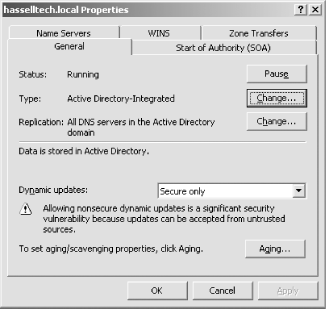
Navigate to the General tab, as shown in Figure 4-20.
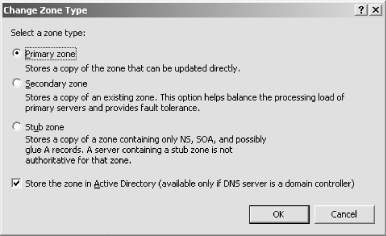
To the right of the Type entry—it should now say either Primary or Secondary—click the Change button. The Change Zone Type screen will appear, as shown in Figure 4-21.
Check the Store the zone in Active Directory checkbox.
Click OK.
You’ll note that your options expand once you’ve converted to Active Directory-integrated zones. Go back to the zone’s properties, and on the General tab, note a couple of things:
The Dynamic Updates field now allows Secure Only updates.
You have options for replicating zone changes throughout all domain controllers in Active Directory.
Let’s focus on the latter for a moment.
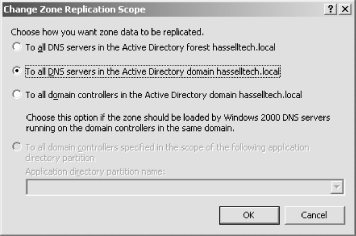
Windows Server 2003 introduces a new feature that allows you to tune how Active Directory replicates DNS information to other domain controllers. Click the Change button beside the Replication field on the zone properties, and you’ll be presented with the Change Zone Replication Scope screen as shown in Figure 4-22.
The default setting is “To all domain controllers in the Active Directory domain,” which instructs Windows to behave exactly as it did in Windows 2000 Server: replicate DNS information to all domain controllers in Active Directory, regardless of whether they’re actually running the DNS service. Obviously, if you have 20 domain controllers in your domain, but only three domain controllers that run DNS, this is a lot of replication traffic that is just wasted. On this screen, you can select to replicate the DNS information only to domain controllers running DNS in either the forest or the domain. This is very helpful, and for large organizations, it should cut down on WAN traffic.
Get Learning Windows Server 2003 now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.