Exploring Federated Security
A federated security model supports the delegation of authentication or authorization activities such that applications and services can authorize calls based on a federated identity. This identity, usually represented by a security token, is expected to contain the necessary information to identify the caller or authorize access to features. The key participants in a federated security model are:
- Subject
The calling application, user, or entity that is described by a federated identity.
- Relying Party (RP)
Services that rely on a federated identity to authorize access to features.
- Identity Provider (IP)
A service that authenticates or authorizes calls and issues a federated identity vouching for the subject. This is also called a security token service.
Figure 7-11 illustrates the typical flow of communication between these three parties. The subject authenticates to the identity provider, who then issues a federated security tokenâwhich represents proof that the subject has been authenticated. The token is then presented to the relying party for authentication and authorization. For this to work, a trust relationship must exist between the relying party and identity provider, as well as between the subject and the identity provider.
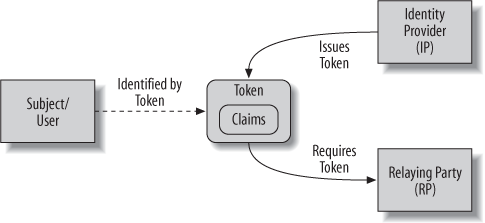
Figure 7-11. Interaction between the subject, identity provider, and relying party in a federated security model
Federated security ...
Get Learning WCF now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

