Kerberos and NAT
The next firewall scenario to consider is pictured in Figure 6-5. In this scenario, all of the KDCs and application servers are behind a corporate firewall, with publicly accessible, routable IP addresses. Clients are located outside of the corporate firewall but live in private IP address space behind a small NAT firewall.
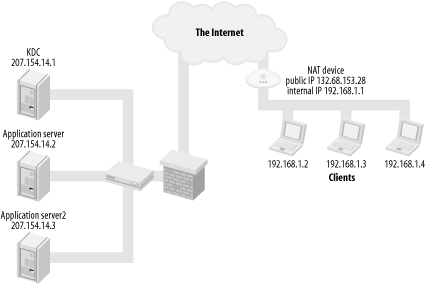 |
Network Address Translation, or NAT, enables multiple machines to share a single IP address. In a NAT setup, clients inside of the NAT device have private, non-routable IP addresses, as defined in RFC 1918. These IP addresses, while valid, are not directly accessible to the Internet at large. The NAT device takes care of relaying requests between the internal machines and the larger Internet. NAT presents a problem to Kerberos since ticket requests contain the requestor’s IP address. Because the clients requesting tickets in this case are using NAT, the IP address they provide to the KDC will be nonroutable. Since the private address on the ticket does not match the public address of the NAT device, Kerberized services will not honor any tickets issued for NAT clients.
For example, you have a user on a cable modem with a small NAT device. The public IP address of the NAT device is 132.68.153.28, and the internal network is the RFC 1918 range 192.168.1.0 to 192.168.1.255. ...
Get Kerberos: The Definitive Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

