Enterprise Network Roles
Rather than revisit each design from the last chapter, let’s use a simpler reference design. Our new reference design contains five types of devices, each used to describe the device roles in the enterprise network. Listing them from the outside of the enterprise network to the inside, the five devices are: the screening router, the security gateway, the Internet border router, core routers, and the access routers (see Figure 3-1). The term “router” is used here very loosely; in some cases an Ethernet switch is implemented in the reference position in enterprise networks.
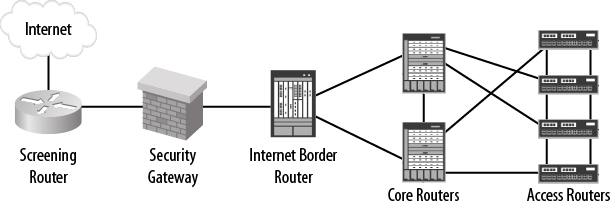
Figure 3-1. Enterprise reference diagram
Of course, enterprise networks vary widely in their implementations. Some networks do not have all these reference devices, and some have other devices not defined here. The choice of device type is often decided in the topmost layers of the protocol stack (sometimes called layers 8 and 9, or politics and cost). Our device recommendations are primarily based on features and size, and take into account those wide-swinging variables, politics and cost.
Screening Router
The classical screening router provides a buffer between the “private” networks and the Internet, with its principal function to protect the other devices from attacks originating on the Internet. These functions include but are not limited to:
- Firewall filters
The screening router implements ...
Get Junos Enterprise Routing, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

