Chapter 5. The Digital Identity Lifecycle
When I was in grade school, our class captured a caterpillar and placed it in a jar with some leaves to see what would happen. Of course, in time, the caterpillar spun a cocoon and the little jar became pretty boring. But our teacher encouraged us to keep watching, and one morning, we were thrilled to see a large moth in the bottle. This simple experiment clearly illustrated to me that the moth and the caterpillar were the same creature at different stages of its life.
Scientists use lifecycles to connect the seemingly unconnected. I'm a big fan of lifecycles in analyzing information technology problems for the same reason. Lifecycles help define all of the phases of a problem or project so that they can be dealt with holistically rather than piecemeal. In addition, lifecycles are useful for categorizing activities associated with the process.
Digital identities have lifecycles, as shown in Figure 5-1. The digital identity lifecycle is applicable regardless of whether we're discussing a complex identity system for a large business or the accounts on a home computer. Understanding how the digital identity lifecycle plays out on every system in the enterprise, and in the enterprise as a whole, is crucial when creating a digital identity management strategy.
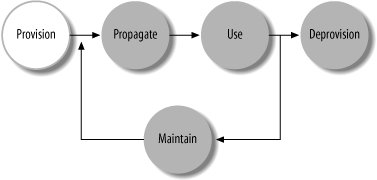
Figure 5-1. Digital identity management lifecycle
Briefly, a digital identity starts ...
Get Digital Identity now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

