9.4 DES KEY SCHEDULE
Three arrays PC-1, PC-2, and KS specify the 48 key bits that are used on each round (Tables 9.14–9.16). The DES key schedule starts with the 56-bit user key k = (k0, k1, …, k55) and derives 16 internal keys ki = (ki, 0, ki, 1, …, ki, 47) with 0 ≤ i < 16, as shown in Figure 9.5. The 48-bit internal key ki used on the ith round is derived as follows:
- KS-1: The user key k is inserted in two 28-bit registers [C, D] according to (PC-1).

- KS-2: [C0, D0] is the initial state of the registers [C, D].
- KS-3: At the start of the ith round, the combined register-pair [Ci − 1, Di − 1] is left-circular shifted by KS[i] positions, producing [Ci, Di]. For example,

- KS-4: ki is derived from the 28 bits of the concatenation of [Ci, Di] according to (PC-2).

Each bit of the user key is used about 13.7 times in a DES-encipherment. The key schedule is designed to use the key bits of k in as uniform a manner as possible.
TABLE 9.14 PC-1
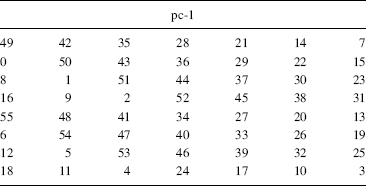
TABLE 9.15 PC-2
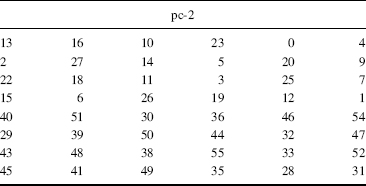
TABLE 9.16 DES Key Shifts
It is ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

