3.5 PRUNING FROM THE TABLE OF ISOMORPHS
We identify the repeated trials of the experiment ∈ with the generation of plaintext with letters in the generic alphabet ![]() by the iid language model with probabilities π(i) = Pr{X = i} for 0 ≤ i < m.
by the iid language model with probabilities π(i) = Pr{X = i} for 0 ≤ i < m.
To test if the ciphertext r-gram v is an isomorph of the plaintext u, the ciphertext letter counts {Nvi} are compared to the plaintext letter probabilities using the χ2-statistic:
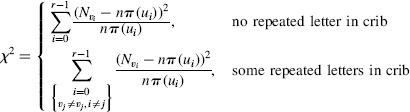
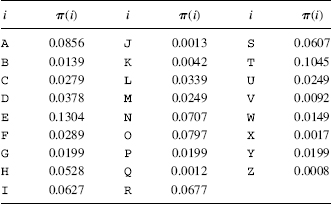
Table 3.5 lists the count of 1-grams {Ni} and their frequencies f(i) = Ni/n in the ciphertext cipherEx3.1. Table 3.6 gives the probabilities {π(i)} of 1-grams derived from a large sample English language text. The plan is to now use the χ2-test to associate the seven high-frequency ciphertext letters in Table 3.5:
TABLE 3.5 Letter Counts and Frequencies in cipherEx3.1
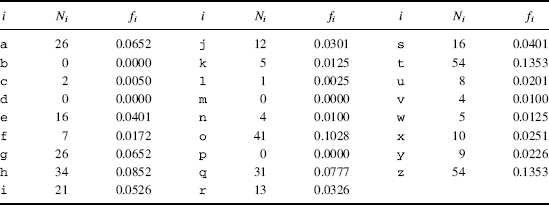
TABLE 3.6 1-Gram English-Language Plaintext Probabilities
![]()
with seven of the nine plaintext letters of highest probability from Table 3.6:
A correspondence between t, z, o, h and some subset of E, T, A, O, N, ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

