2.10 CODA
Although cribbing and Markov scoring often permit a successful attack on columnar transposition ciphertext, there are several possible modifications of the rules that may strengthen the encipherment method.
M1. The rectangular shape of X might be replaced by a triangle:
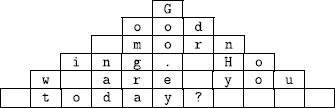
The plaintext Good morning. How are you today? Would be read into X by rows and read out according to a transposition τ. There are details to be supplied so that τ does not depend on the length of the plaintext.
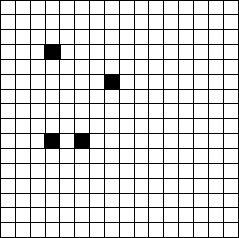
Figure 2.5 A grille.
M2. The rectangular shape of X might be retained, but a grille as shown in Figure 2.5 would be used to construct X. The plaintext would read into X as before except that certain (perhaps keydependent) positions in X would be skipped.
M3. The rectangular shape of the array might be retained, but encipherment would involve two steps:
(a) The plaintext would be read into an array X1 of width N1 and read out according to the transposition τ = (τ0, τ1, …, τN1 − 1);
(b) The resulting intermediate ciphertext would be read into an array X2 of width N2 and read out according to the transposition τ = (τ0, τ2, …, τN2 − 1).
We will not pursue the analysis of any of these modifications, leaving them to the interested reader.
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

