16.5 SHAMIR'S AUTONOMOUS KEY EXCHANGE
In unpublished work, Adi Shamir proposed a key exchange protocol that depends on the secure exchange of no secret information. The following steps exchange a key between User_ID[i] and User_ID[j]:
| 0. |
p is a (known) prime; ki and kj are the (secret) keys of User_ID[i] and User_ID[j]. It is assumed that 1 = gcd{ki, p − 1} = gcd{kj, p − 1} so that both ki and kj have multiplicative inverses modulo p − 1
By Fermat's Little Theorem
|
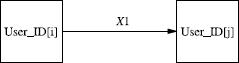
Figure 16.3 Step #1 in Shamir's autonomous key exchange.
- User_ID[i] (the initiator) selects a session key X0 and performs the exponentiation
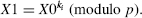
X1 is transmitted to User_ID[j] (Fig. 16.3).
- User_ID[j] performs the exponentiation
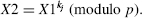
X2 is transmitted to User_ID[i] (Fig. 16.4).
- User_ID[i] performs the exponentiation
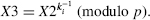
X3 is transmitted to User_ID[j] (Fig. 16.5).
- User_ID[j] performs the exponentiation
Proposition 16.2: ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

