It’s an unwritten law that you can’t write a book about personal privacy without quoting Sun Microsystems CEO Scott McNealy’s infamous 1999 statement: “You have zero privacy anyway. Get over it.”
There, I’ve done my duty. But before we move on, let’s examine his statement a little more closely.
Fact is, McNealy was wrong. Although privacy protections in this country are not exactly plentiful, this isn’t 1984 or The Trial—at least, not yet. There’s no video camera trained on you in your home, recording your every moment. (Or if there is, it’s a webcam and you probably put it there.) You enjoy relative freedom of movement, though you may be frisked or required to show your ID to board an airplane.
Your bank account, medical records, and school transcripts are all more or less protected by Federal and state law; there’s even a law that keeps nosy people from obtaining the names of the videos you rent. Though there are few limits on how corporations can use your data, the courts are starting to force them to follow the policies laid out in their own privacy statements. And while FBI agents can theoretically demand your library records or bookstore receipts if they decide you pose a terrorist threat, odds are pretty good that no one else knows you’re reading this book right now.
The trouble is, there’s just not enough privacy. There are huge gaps in our legal protections, and the laws we do have are generally half measures at best. (And unlike many European countries, we lack anything resembling a federal Privacy Commissioner.) The privacy that remains is rapidly being eroded by technology, commercial interests, and increasing government surveillance.
In this chapter, I’ll outline the threats to your privacy and how we’ve gotten in this mess. The rest of this book is devoted to what you can do about it. It all starts with a big noisy machine that’s probably sitting on or near your desk right now.
Once upon a time, when you needed to deposit money in your checking account, you visited the bank. If you were hungry for something new to read, you went to the bookstore. When you purchased music or rented a movie it came home on a shiny silver disc. Had a medical question? You called your doctor or pulled a book off a shelf. When you wanted to have a private conversation with a friend, you called them on the phone or sent a letter.
Today, you may be doing all of the above online. It’s incredibly convenient and often cheaper. But the threat to your privacy increases exponentially.
All of a sudden, your personal finances, the books you bought at Amazon, the music and video files you downloaded, the medical web sites you visited, the search terms you typed into Google or Yahoo, your email and instant message conversations—all are concentrated in a single point of entry: your computer.
A computer is a secretary who jots everything down, takes perfect notes, and never forgets a thing until you tell it to (or the hard disk crashes). Unless you’ve taken steps to protect yourself—and most people don’t—anyone with rudimentary computer skills can sit at your keyboard and learn everything about you in just a few minutes. They can look at your browser history or your cookie files, scan your document folders, peek inside your personal finance software, and so on. They can build a highly detailed dossier of your hobbies and interests, your physical ailments, your fiscal health, and any naughtiness you may have been up to. No hacking required.
This also includes any law enforcement agencies, divorce attorneys, and possibly your boss—anyone with an adversarial interest and/or the legal right to impound your computer can see what you’ve been up to.
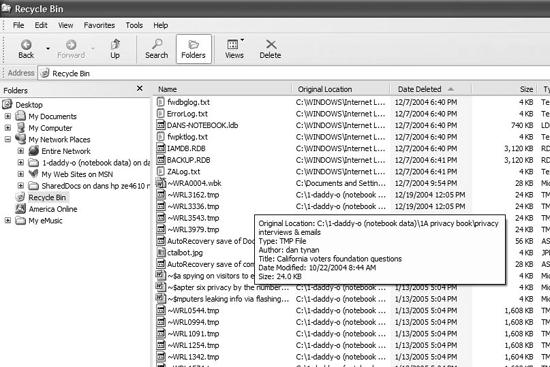
Oh, and those files you deleted? They’re still there (see Figure 1-1). Unless you’re very careful and know precisely what to do, anything that’s been “deleted” can be retrieved fairly easily. (For tips on how to secure your PC, see Chapter 2.)
Get Computer Privacy Annoyances now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.