The Security Perimeter
The discussion to this point has not mentioned the specific technology used to enforce operational and organizational security or a description of the various components that constitute the organization’s security perimeter. If the average administrator were asked to draw a diagram depicting the various components of her network, the diagram would probably look something like Figure 2-1.
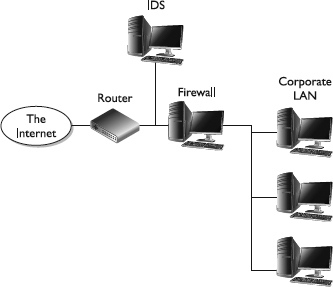
Figure 2-1 Basic diagram of an organization’s network
This diagram includes the major components typically found in a network. A connection to the Internet generally has some sort of protection attached to it such as a firewall. An intrusion ...
Get CompTIA Security+ All-in-One Exam Guide (Exam SY0-301), 3rd Edition, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

