Network Security
Amazon’s cloud has no perimeter. Instead, EC2 provides security groups that define firewall-like traffic rules governing what traffic can reach virtual servers in that group. Although I often speak of security groups as if they were virtual network segments protected by a firewall, they most definitely are not virtual network segments, due to the following:
Two servers in two different Amazon EC2 availability zones can operate in the same security group.
A server may belong to more than one security group.
Servers in the same security group may not be able to talk to each other at all.
Servers in the same network segment may not share any IP characteristics—they may even be in different class address spaces.
No server in EC2 can see the network traffic bound for other servers (this is not necessarily true for other cloud systems). If you try placing your virtual Linux server in promiscuous mode, the only network traffic you will see is traffic originating from or destined for your server.
Firewall Rules
Typically, a firewall protects the perimeter of one or more network segments. Figure 5-2 illustrates how a firewall protects the perimeter.
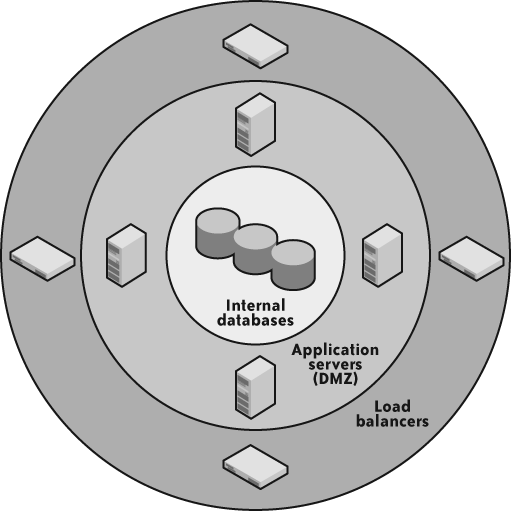
A main firewall protects the outermost perimeter, allowing in only HTTP, HTTPS, and (sometimes) FTP[13] traffic. Within that network segment are border systems, such as load ...
Get Cloud Application Architectures now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

