Circumventing an IPS/IDS
An attacker has an objective, and it is likely that he does not want to be stopped or seen. So, if you have IPS/IDS in place, an attacker may try to evade detection of his activities by the IPS/IDS. Table 17-6 describes evasion methods an attacker may try to use and Cisco options to counter these evasion techniques.
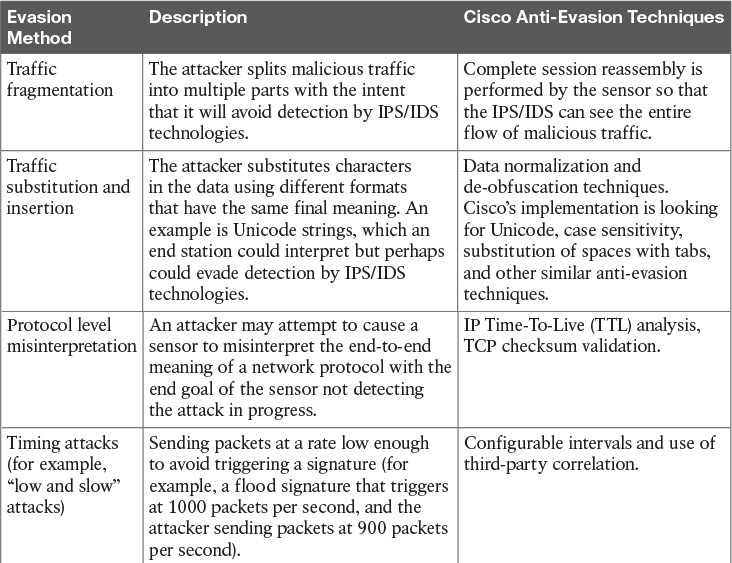
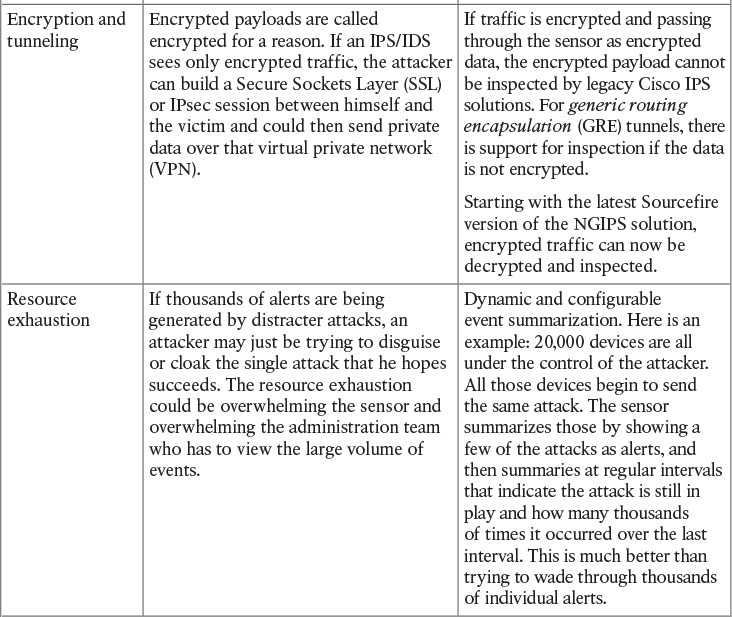
Table 17-6 IPS/IDS Evasion Techniques
Get Santos:CCNA Sec 210-260 OCG now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

