Reverse Engineering from ACL to Address Range
For this second question set, look at the existing access-list commands in Table J-2. In each case, make a notation about the exact IP address, or range of IP addresses, matched by the command.
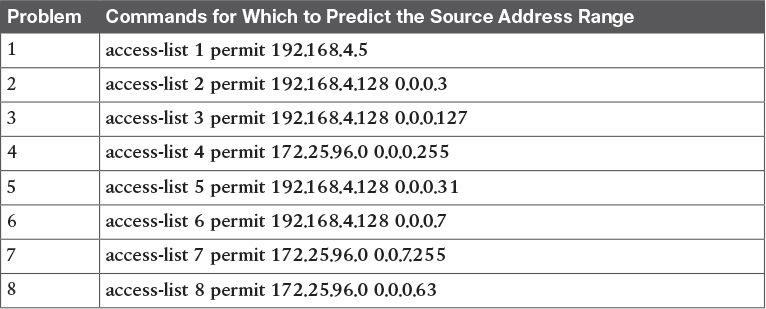
Table J-2 Finding IP Addresses/Ranges Matching by Existing ACLs
Note
You can only rely on the method of adding these numbers together (as shown in Chapter 22 of the ICND1 book) if you know that the access-list command comes from the router and specifically is not what someone simply wrote on a piece of paper. In this case, you can assume that the statements in Table J-2 came from a router.
Get CCENT/CCNA ICND1 100-101 Official Cert Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

