Man in the Middle
Earlier in this book, in Chapter 4, we looked at how hackers can use man-in-the-middle attacks (MITM) to capture your login credentials, API keys, and other personal information via a proxy. We can try to do the same to make sure that third-party SDKs are reporting data back to the server securely. Ideally we’d want to make sure the app is sending things back to the third-party back-end servers using HTTPS. Figure 7-7 shows an example of an app that looks like it was built for collecting information and, worse still, is communicating insecurely over HTTP.
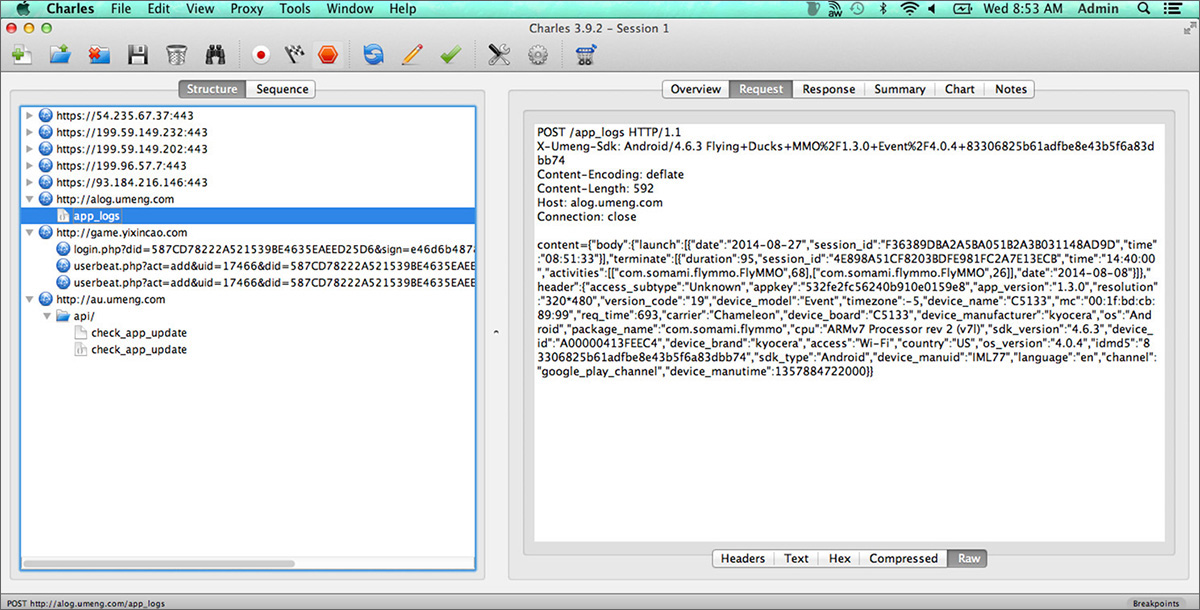
Figure 7-7 MITM attack on Flying Ducks Android App
Figure 7-8 shows ...
Get Bulletproof Android™: Practical Advice for Building Secure Apps now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

