DexGuard
One of the best descriptions on the different levels of obfuscation comes from Christian Collberg’s paper, “A Taxonomy of Obfuscating Transformations,” which you can find at https://researchspace.auckland.ac.nz/bitstream/handle/2292/3491/TR148.pdf. A Java list of obfuscation classifications from the paper can be found in Table 2-1.
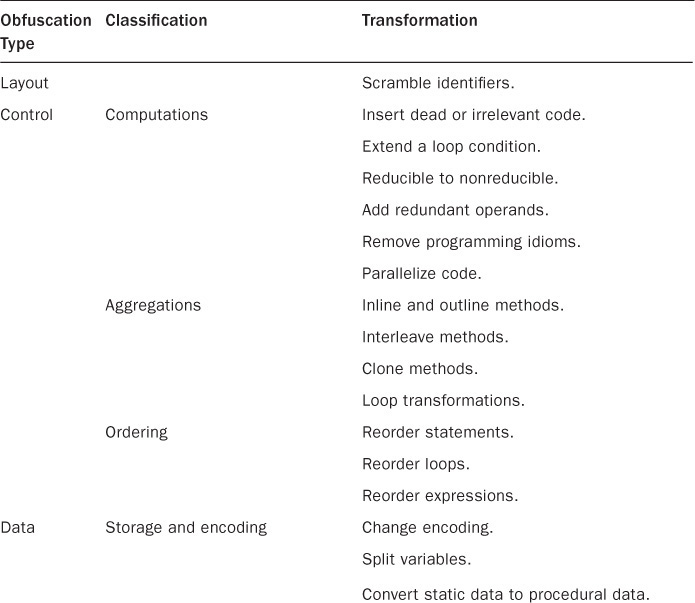

Table 2-1 Taxonomy of Obfuscations
There are four major categories of obfuscation: layout, control, data, and preventative. We’ve already seen a good example where the identifiers have been scrambled, which ...
Get Bulletproof Android™: Practical Advice for Building Secure Apps now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

