The Perils of Protected Mode
The arrival of protected mode brings a whole new system of memory management into play, with another layer of complexity added on top of the physical address space. In protected mode, paging can be enabled, which allows the rearrangement of the constituent 4 KB blocks of the physical address space. This rearrangement is controlled by a sequence of tables held in memory that can be dynamically modified by the code running on the machine. Figure 9-4 shows the path followed on a complete page translation.
In principle, every memory access on the machine will require a full lookup sequence through this paging structure to find the physical address that the given linear address maps to. As this process is so convoluted and costly, a real machine will cache the result of these lookups in translation look-aside buffers (TLBs). In addition to these added layers of indirection, there are extra protection features with memory paging. Each mapped page can be given a user or supervisor and a read or read/write status. Code that attempts to access pages without sufficient privileges, or tries to access pages that simply do not exist, results in the raising of a processor exception in a manner analogous to a software interrupt.
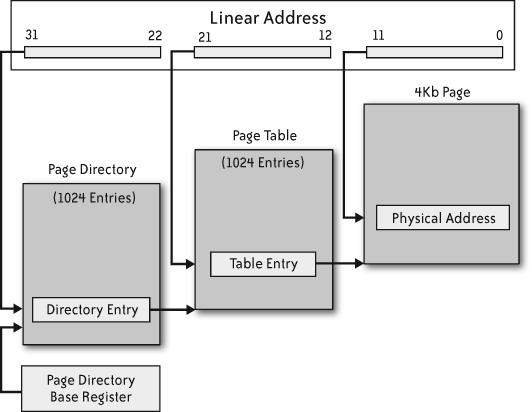
Figure 9-4. Paging mechanism of the IA32 architecture (4 KB pages only)
To optimize such a structure, it is clear that our first tactic should ...
Get Beautiful Architecture now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

