Food for Thought
The technique of phase-space analysis is useful in fields that go far beyond sequence-number generation. Other parameters that are chosen pseudo-randomly or according to some internal scheme—such as IP packet ID fields, DNS request identifiers (as shown in Figure 10-16), application-generated “secret” cookies that identify user sessions, and so on—can be analyzed successfully, either to find flaws in a design or to identify an implementation and simplify further analysis or facilitate an attack.
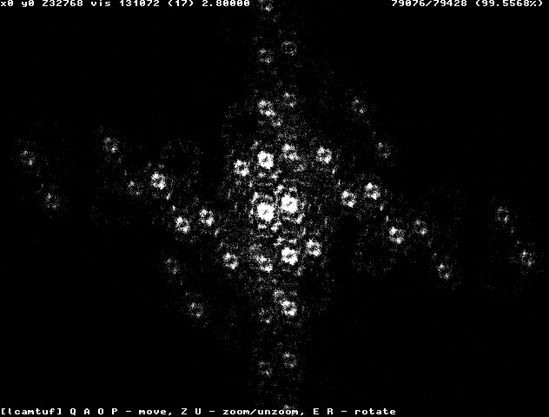
Figure 10-16. An interesting attractor pattern for Linux name-resolver implementation
Some work in this direction had been done or is under ...
Get Silence on the Wire now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

