The ultimate purpose of this book is to be the single, most complete source for working knowledge related to Juniper Networks enterprise routing. Although you wonât find much focus on actual packet formats and fields, topics for which there is already plentiful coverage on the Internet and in bookstores, you will find how to effectively deploy JUNOS technology in your network.
Hereâs a short summary of the chapters and what youâll find inside:
- Chapter 1
This chapter provides an overview of the hardware and software architecture on Juniper enterprise routers, as well as an overview of the JUNOS CLI for both new and experienced users.
- Chapter 2
This chapter provides an overview of JUNOS interface organization. Then it dives into some of the most common interface types and configurations seen in networks today. Finally, it concludes with a troubleshooting section with real-life scenarios seen every day.
- Chapter 3
This chapter provides a condensed but comprehensive overview of JUNOS Protocol Independent Properties (PIPs), such as static and aggregate route, and of routing policy, which is used to control route advertisement, redistribution, and attribute manipulation.
- Chapter 4
This chapter provides a detailed review of Interior Gateway Protocol (IGP) operation, and then focuses on multivendor deployments of the Routing Information Protocol (RIP) and Open Shortest Path First (OSPF). The material also focuses on IGP migration strategies and includes an EIGRP-to-OSPF migration case study.
- Chapter 5
After providing a detailed review of what the Border Gateway Protocol (BGP) is and how it can benefit an enterprise, this chapter provides a series of case studies that build in complexity, starting with a single homed network with no Internal BGP (IBGP) speaker and ending with a multihomed-to-multiple-providers scenario, to include a redundant IBGP route reflection design that avoids running IBGP on all internal routers. The policy treatment is focused on practical enterprise routing goals, and it details both inbound and outbound policy that includes autonomous system (AS) path regex matching and BGP attribute manipulation.
- Chapter 6
This chapter provides an overview of a large variety of security concepts and the tools available to deploy them. These tools include user authentication and authorization, remote access, firewall filters, policers, Unicast Reverse Path Forwarding, the Simple Network Management Protocol (SNMP), and syslog.
- Chapter 7
This chapter provides an overview of the Layer 2 and Layer 3 services that can be deployed on a Juniper Networks router. Layer 2 services include features such as link bundling and Generic Routing Encapsulation (GRE), whereas Layer 3 services include stateful firewalls, IPSec, and Network Address Translation (NAT). This chapter also lays the CLI foundation to discuss more scenarios in Chapter 8.
- Chapter 8
This chapter dives into the complex scenarios of the features discussed in Chapter 7. It walks through various deployed NATs, IPSec virtual private networks (VPNs), IPSec over GRE, and all possible Layer 3 services combined.
- Chapter 9
This chapter provides an overview of IP class of service (CoS) and includes a detailed primer on IP DiffServ. The material then details the similarities and differences in CoS handling between the J-series and M7i routers, which is a common source of confusion. A practical CoS case study serves as the foundation for CoS deployment and operational verification. The chapter also demonstrates the J-series-specific Virtual Channel CoS feature.
- Chapter 10
Multicast tends to see little deployment and is a common area of confusion. This chapter details IP multicast concepts, provides an overview of multicast protocols, and then demonstrates several Physical Interface Module (PIM) sparse mode scenarios, to include PIM sparse mode with static, bootstrap, and Anycast-RP. Through all the examples, practical verification and fault isolation steps are provided.
- Chapter 11
This hot-off-the-press chapter includes the first official coverage of the new JUNOS software with enhanced services release. This chapter gives you the heads-up needed to understand what JUNOS software with enhanced services offers, how to migrate from JUNOS to JUNOS software with enhanced services, and the various things you need to know before deploying JUNOS software with enhanced services.
In addition, you can also use this book to attain one of the Juniper Networks certification levels related to enterprise routing. To that end, each chapter in the book includes a set of review questions and exam topics that have been covered, all of it designed to get you thinking about what youâve just read and digested. If youâre not in the certification mode, the questions will provide a mechanism for critical thinking, potentially prompting you to locate other resources to further your knowledge.
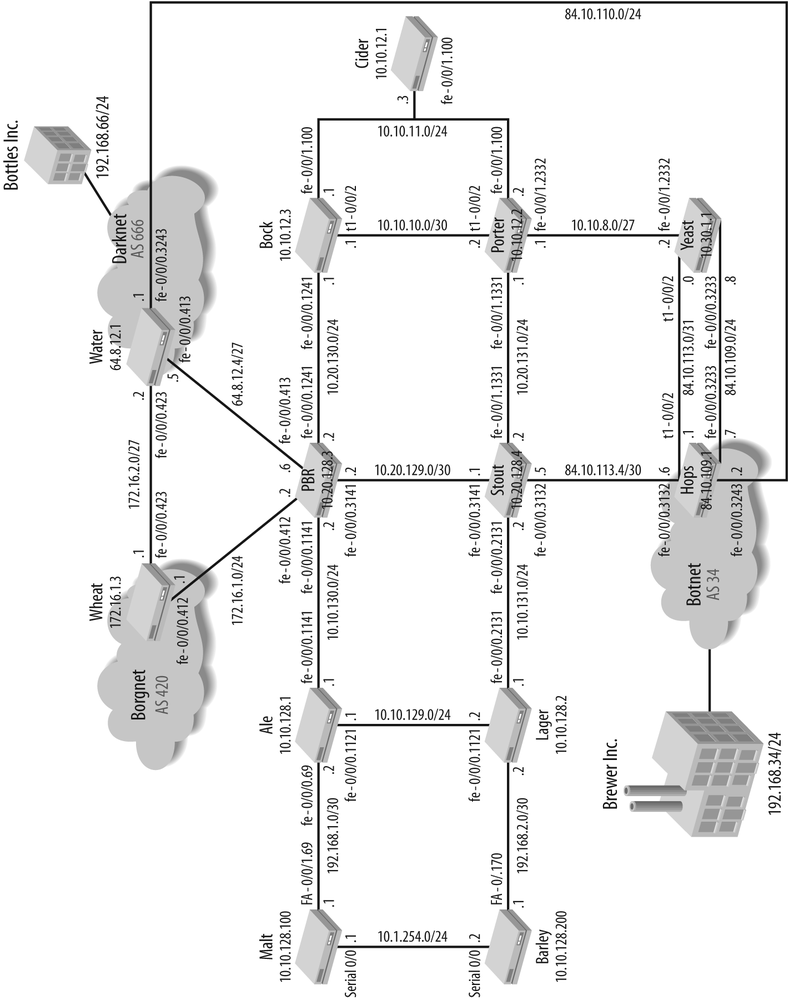
Figure 1 displays the topology of the book that appears beginning in Chapter 3. It consists of 11 J-series routers running version 8.0R1.9 and 2 Cisco routers running IOS Release 12.3(15b). The Cisco routers are primary employed in Chapter 4, where they are used for both RIP interoperability and as part of an EIGRP-to-OSPF migration exercise. The topology uses only Fast Ethernet and T1 interfaces; however, other interface types are examined in Chapter 2. You might recognize the hostnames of the routersâthey all relate to a beverage that was created more than 7,000 years ago (with evidence to consumption) in Mesopotamia. The names are chosen due to the international appeal of the resultant product and for the resultant food value only, as beer is an excellent way to preserve the nutritional value of grain.
Get JUNOS Enterprise Routing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.