If you have ever ridden the London Underground, you are familiar with the phrase “Mind the gap.” You are implored to mind the gap between the platform and the moving Underground cars. The subway platform and the car doors should line up horizontally and vertically, but they usually do not. In some places the gap between the two can be significant. So, you need to watch your step.
We could use the concept of minding the gap as an operative phrase about cloud computing and its security. Ideally, these two concepts, cloud computing and the security that it affords, should align, but they usually do not. It has become a common mantra in the high-technology industry to chant “cloud computing good” while at the same time saying “cloud security bad.” But what does that really mean? Exactly what is wrong with security in cloud computing?
The purpose of this book is to answer those questions through a systematic investigation of what constitutes cloud computing and what security it offers. As such, this book also explores the implications of cloud computing security on privacy, auditing, and compliance for both the cloud service provider (CSP) and the customer. Is security in cloud computing a bad thing? The answer depends on what you use cloud computing for, and your expectations. If you are a large organization with significant resources to devote to a sophisticated information security program, you need to overcome a number of security, privacy, and compliance challenges that we explore later in the book. However, if you are a small to medium-size business (SMB), the security of cloud computing might look attractive, compared to the resources you can afford to spend on information security today.
To understand what cloud computing is and is not, it is important to understand how this model of computing has evolved. As Alvin Toffler notes in his famous book, The Third Wave (Bantam, 1980), civilization has progressed in waves (three of them to date: the first wave was agricultural societies, the second was the industrial age, and the third is the information age). Within each wave, there have been several important subwaves. In this post-industrial information age, we are now at the beginning of what many people feel will be an era of cloud computing.
In his book The Big Switch (W.W. Norton & Co., 2008), Nicholas Carr discusses an information revolution very similar to an important change within the industrial era. Specifically, Carr equates the rise of cloud computing in the information age to electrification in the industrial age. It used to be that organizations had to provide their own power (water wheels, windmills). With electrification, however, organizations no longer provide their own power; they just plug in to the electrical grid. Carr argues that cloud computing is really the beginning of the same change for information technology. Now organizations provide their own computing resources (power). The emerging future, however, is one in which organizations will simply plug in to the cloud (computing grid) for the computing resources they need. As he puts it, “In the end the savings offered by utilities become too compelling to resist, even for the largest enterprises. The grid wins.” In fact, Part 2 of his book is about “living in the cloud” and the benefits it provides. (Carr also discusses at length some of the perceived negative consequences to society of this big switch, specifically some of the darker aspects this change brings to society.)
Carr is not alone in arguing for the benefits of cloud computing, but he has put forth what is arguably the most articulate statement of those benefits thus far. And although he focuses specifically on the economic benefits of cloud computing, he does not discuss information security problems associated with “the big switch.” We do, and that is the purpose of this book: to articulate security and privacy issues associated with “the big switch” to cloud computing.
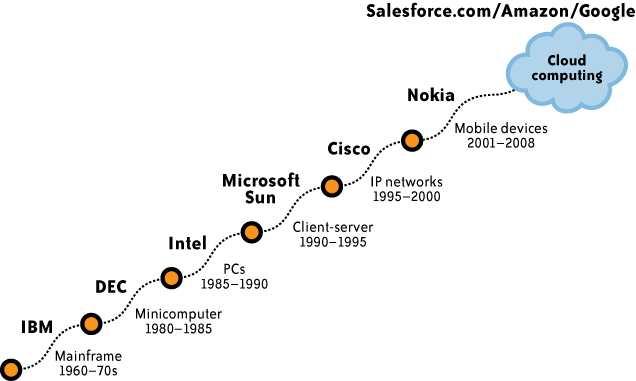
As we noted earlier, within each wave there are subwaves, and there have already been several within the information age, as Figure 1-1 shows. We started with mainframe computers and progressed to minicomputers, personal computers, and so forth, and we are now entering cloud computing.
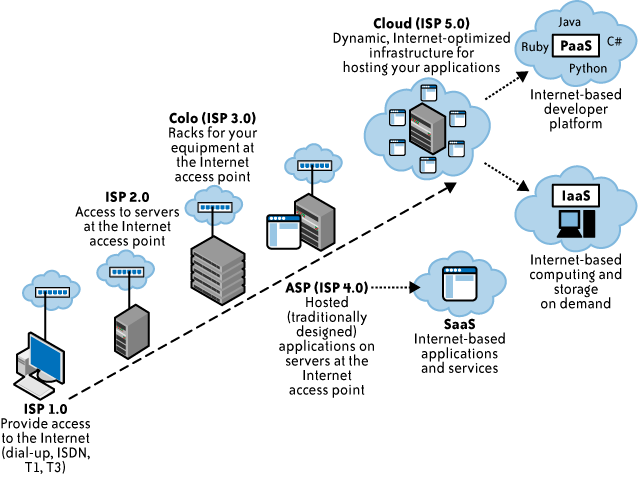
Another view illustrates that cloud computing itself is a logical evolution of computing. Figure 1-2 displays cloud computing and cloud service providers (CSPs) as extensions of the Internet service provider (ISP) model.
In the beginning (ISP 1.0), ISPs quickly proliferated to provide access to the Internet for organizations and individuals. These early ISPs merely provided Internet connectivity for users and small businesses, often over dial-up telephone service. As access to the Internet became a commodity, ISPs consolidated and searched for other value-added services, such as providing access to email and to servers at their facilities (ISP 2.0). This version quickly led to specialized facilities for hosting organizations’ (customers’) servers, along with the infrastructure to support them and the applications running on them. These specialized facilities are known as collocation facilities (ISP 3.0). Those facilities are “a type of data center where multiple customers locate network, server, and storage gear and interconnect to a variety of telecommunications and other network service provider(s) with a minimum of cost and complexity.”[2] As collocation facilities proliferated and became commoditized, the next step in the evolution was the formation of application service providers (ASPs), which focused on a higher value-added service of providing specialized applications for organizations, and not just the computing infrastructure (ISP 4.0). ASPs typically owned and operated the software application(s) they provided, as well as the necessary infrastructure.
Although ASPs might appear similar to a service delivery model of cloud computing that is referred to as software-as-a-service (SaaS), there is an important difference in how these services are provided, and in the business model. Although ASPs usually provided services to multiple customers (just as SaaS providers do today), they did so through dedicated infrastructures. That is, each customer had its own dedicated instance of an application, and that instance usually ran on a dedicated host or server. The important difference between SaaS providers and ASPs is that SaaS providers offer access to applications on a shared, not dedicated, infrastructure.
Note
The acronym “SaaS” is used for both software-as-a-service and security-as-a-service, which is discussed in Chapter 10. However, all uses of “SaaS” in this book, with the exception of Chapter 10, are to software-as-a-service.
Cloud computing (ISP 5.0) defines the SPI model, which is generally agreed upon as providing SaaS, platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS). For more information about these service models, see Chapter 2.
With increasing attention, some would say hype, now being paid to cloud computing, companies are increasingly claiming to be “cloudy.” Suddenly, many companies are claiming to operate “in the cloud.” Serious cloud washing is underway. Similarly, a number of computing groups have announced their efforts to promote some facet of cloud computing. Some of these groups are established (e.g., the National Institute of Standards and Technology efforts to promote standardization in cloud computing), and some of them are brand new, having emerged only with the appearance of this new computing model (e.g., the Cloud Security Alliance’s promotion of security in cloud computing, or the Open Cloud Manifesto’s promotion of cloud interoperability). Many other groups have also announced efforts dedicated to cloud computing, such as the Distributed Management Task Force (DMTF); the Information Technology Association of America, a high-technology industry association; and the Jericho Forum, an international information security thought leadership association, among many others.
Cloud computing is a nascent and rapidly evolving model, with new aspects and capabilities being announced regularly. Although we have done our best in the forthcoming chapters to provide a comprehensive and timely look at these issues, no doubt there are areas that we have not addressed or aspects that might have changed already. With that in mind, we encourage your feedback. We also invite you to participate in an ongoing discussion with us about the issue of cloud computing at http://www.cloudsecurityandprivacy.com.
[2] Wikipedia definition of collocation facility: http://en.wikipedia.org/wiki/Co-location_facility.
Get Cloud Security and Privacy now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.