9.1. Firewalls and E-speak Services
The firewall works well to secure the e-Speak services behind it. The network administrator will configure the firewall to grant access, depending on the entity trying to access the internal assets and services. For example, company policies might grant unrestricted intranet access; these policies can be modified to allow access to an authorized third-party. This third-party entity could be a co-development partner or a vendor with special ties. Figure 9.1 depicts this type of access policy.
Figure 9.1. Punching firewall holes.
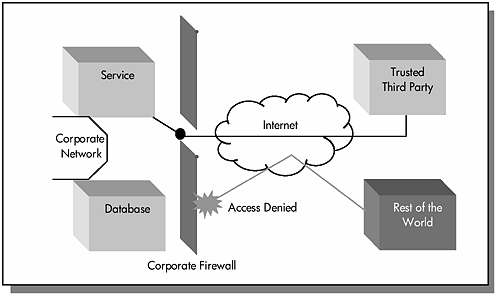
However, companies that do allow access to external entities need to go through ...
Get Web Services: A Java™ Developer’s Guide Using E-Speak now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

