Although the two examples in the preceding section involved standalone programs, increasingly there is interest in using downloaded programs to extend the capabilities of web browsers. One way to do this is with helper applications , such as the RealAudio player. Another way is through the use of plug-ins.
Plug-ins were introduced with Netscape Navigator as a simple way of extending browsers with executable programs that are written by third parties and loaded directly into Netscape Navigator. One of the simplest uses for plug-ins is to replace helper applications used by web browsers. Instead of requiring that data be specially downloaded, saved in a file, and processed by a helper application, the data can be left in the browser’s memory pool and processed directly by the plug-in. But plug-ins are not limited to the display of information. In the fall of 1996, Microsoft released a plug-in that replaced Netscape’s Java virtual machine with its own. And PGP, Inc., is developing a plug-in that adds PGP encryption to Netscape Communicator’s email package.
Plug-ins are manually downloaded by the web user and stored in a special directory located in the Netscape Navigator program directory. The web browser scans this directory when it starts up to discover what plug-ins are available.
Two popular plug-ins are the Macromedia Shockwave plug-in, which can play animated sequences, and the Adobe Acrobat plug-in, which lets Navigator display PDF files. Both of these plug-ins have been used since shortly after the introduction of Netscape’s plug-in architecture.
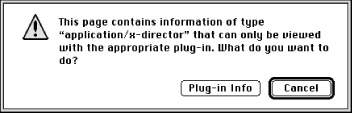
When Netscape Navigator encounters a document that requires a plug-in to be properly viewed, Navigator displays a window such as the one in Figure 4.1.
Figure 4-1. Netscape Navigator displays a special window when it encounters a document for which a plug-in is required
If the user clicks the “Plug-in Info” button, Navigator switches to a web page that describes the plug-ins that are currently available. At the bottom of the page there is a link for a “security warning.” Follow the link and you’ll see an ominous message:
Plug-in Security Implications
When running network applications such as Netscape Navigator, it is important to understand the security implications of actions you request the application to perform. If you choose to download a plug-in, you should know that:
* Plug-ins have full access to all the data on your machine.
* Plug-ins are written and supplied by third parties.
To protect your machine and its documents, you should make certain you trust both the third party and the site providing the plug-in.
If you download from a site with poor security, a plug-in from even a trusted company could potentially be replaced by an alternative plug-in containing a virus or other unwanted behavior.
...Copyright © 1996 Netscape Communications Corporation
Unfortunately, most users don’t have the necessary tools or understanding to act upon Netscape’s message. Most users wish to view the content of the page in question, and they will download the plug-in and install it no matter what the source. Few realize that a plug-in can do far more damage than simply crashing their computer.
Given Netscape’s warning, how do you evaluate whether or not you should install a plug-in on your computer?
Fundamentally, it is nearly impossible to determine if a plug-in does or does not have hidden security problems. That’s because plug-ins are provided pre-compiled and without source code. Unless you work for the company that creates the plug-in, it is usually not possible to inspect the actual plug-in’s source code. Instead, you must trust the company that makes the plug-in and hope the people there have your best interests at heart.
Of course, the trust that you need to place in the plug-in vendor is fundamentally no different from the trust you place in the company that creates the web browser, the other applications that you run, your computer’s operating system, and the computer’s hardware itself. But whereas there are only a few companies that have the engineering prowess to create a full-featured word processor or web browser, by design many companies can create a plug-in without very much work. And whereas you might not be interested in running a web browser from Midnight Software, you might be willing to give their amazing “web rearranger” software a try. This opens you up to a much larger universe of potential attackers.
There are many ways that your computer might be damaged by a plug-in. For example:
The plug-in might be a truly malicious plug-in, ready to damage your computer when you make the mistake of downloading it and running it.
The plug-in might be a legitimate plug-in, but a copy might have been modified in some way to exhibit new dangerous behaviors. (Netscape Navigator 4.0 has provisions for digitally signing plug-ins. Once modified, a digitally signed plug-in’s signature will no longer verify.)
There might not be a malicious byte of code in your plug-in’s executable, but there might be a bug that can be misused by someone else against your best interests.
The plug-in might implement a general-purpose programming language that can be misused by an attacker.
Consider the Macromedia Shockwave plug-in. In January 1997, Simson learned that the Shockwave plug-in contained instructions for reading and writing directly to the file systems of the computer on which the web browser is running. This would seem to be a security problem. So Simson contacted Macromedia, spoke with an engineer, and was told that the Shockwave plug-in could only read and write to files stored in a particular directory in the Shockwave folder. The engineer said that Macromedia had been very careful to ensure that the plug-in could read and write to no other files on the system. He further said that there was no way to use the system to store executable files.
On March 10, 1997, David de Vitry posted a message to the Bugtraq mailing lists that said the Shockwave plug-in could be used to read email messages stored in the Netscape mail folders. Apparently, the Shockwave GETNETTEXT command can read from many different folders located within the Netscape directory, rather than just Shockwave “preference” files. Reportedly, this Shockwave bug also affected Macromedia’s plug-in with Internet Explorer.
Macromedia said that it would be issuing a bug fix. Unfortunately, there’s no way to know whether or not other security problems are lurking and misunderstood by the company’s own engineers. This is true for every plug-in, not simply Macromedia.
The security problem with the Macromedia plug-in was publicized through a variety of channels, both electronic and print. Presumably, this is the way that Netscape believes plug-in security will be addressed: people who discover problems with plug-ins will publicize them. Other users will know not to install plug-ins that have problems and avoid running them (or de-install them if they were running them already). Certainly some users may fall victim to a malicious program, but it’s hoped that such malicious plug-ins will be quickly exposed. Netscape may be correct, but that may be small comfort for the users who are in the position of discovering such a piece of malware.
Unfortunately, if you are a specific target, you cannot find safety in numbers. It is fairly trivial to create a program that behaves one way for everybody else in the world and another way for you in particular. Such a program could also be programmed to cover its tracks. If you did notice a problem, you might be more likely to ascribe it to a passing bug or strange interaction because no one else would have reported the problem.
Get Web Security and Commerce now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.