A firewall is a device (usually a computer running a specially written or modified operating system) that isolates an organization’s internal network from the Internet at large, allowing specific connections to pass and blocking others. Ideally, firewalls are configured so that all outside connections to an internal network go through relatively few well-monitored locations. In so doing, firewalls are part of an organization’s overall security strategy.
Unfortunately, many organizations have seized upon firewall technology as their sole security strategy. We have seen organizations that realize they have serious security problems on their internal networks—and then attempt to “solve” this problem by simply using a firewall to block external access.
Because firewalls are frequently misused, we are ambivalent about them. We have too often seen firewalls as a substitute for real problem fixing. And because many attacks come from disgruntled or dishonest employees, and not from outsiders, firewalls divert attention from the real problems of network and host vulnerabilities, poor planning, and lack of organizational policies. Thus, firewalls often improve security only a small amount and, in the process, give their owners a false sense of security.
There are some real situations in which to use firewalls. One is that some organizations must use older "legacy systems” that cannot be secured: a firewall can be used to control access to these systems. (Such firewalls should probably be used to control all access to these systems, rather than merely access from outside the organization.) Another reason to use a firewall is that it is much more difficult to track down an attacker who comes from outside a network than one who comes from inside.
Thus, a firewall should only be used to gain additional security that works in conjunction with internal controls—and never as a replacement for them.
If your organization uses a firewall to protect its internal network from external attacks, you have a number of choices of where to locate your web server:
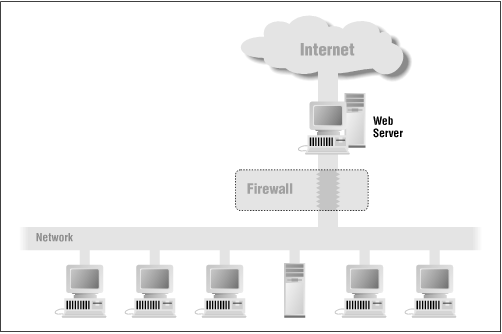
You can locate the web server outside your firewall (see Figure 1.4). The advantage of locating the server outside the firewall is that the web server may be subject to ongoing attacks from rogue Internet users; in the event that the web server is broken into, they will not have gained an increased foothold for launching further attacks against your organization. On the other hand, the web server will not be able to benefit from whatever protection the firewall affords.
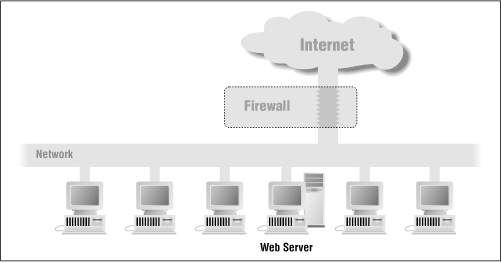
You can place the web server inside your firewall (see Figure 1.5). If you do this, you will need to configure your firewall so that it will pass transactions on TCP port 80, either by directly allowing the packets through or by using a suitable proxying mechanism. The advantage of locating the web server behind your firewall is that the firewall will block outsiders from using other Internet services, such as Telnet and FTP. However, if attackers manage to subvert your web server through a faulty CGI script, they will have full access to your internal network.
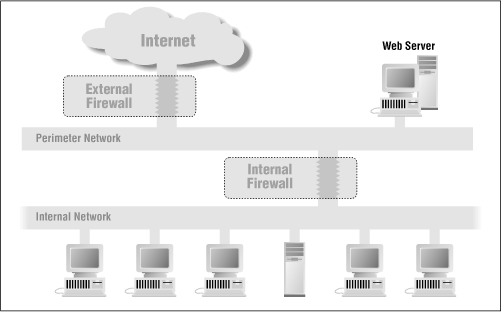
Your third option is that you can use two firewalls: one to shield your internal network and one to shield your web server (see Figure 1.6).
A properly secured web server gains no benefit by being placed inside a firewall. That’s because a properly secured web server offers only two TCP/IP services to the outside world: HTTP on port 80, and HTTP with SSL on port 443. If you placed your web server behind the firewall, you would have to program the firewall to allow incoming connections to ports 80 and 443 from computers on the Internet.
Of course, the computer on which the web server is running may offer other services to the network as well. Administrators need a way of logging into the computer to perform periodic maintenance and update content. While these services can benefit from the added protection of a firewall, those added protections can easily be incorporated directly on the web server’s host. For example, most firewalls block incoming Telnet sessions or provide a mechanism for additional authentication using smart cards or one-time passwords. However, services can be selectively blocked and additional authentication mechanisms can be employed directly at the host by installing and properly configuring Wietse Venema’s TCP Wrapper on UNIX-based systems, or correctly enabling access control lists in Windows NT 4.0. Support for token-based authentication, such as using Security Dynamics SecureID cards, can be added to practically any network-based computer. (We describe many of these strategies in later chapters.)
Another reason to locate the web server outside your firewall is that your web server is one of the most likely computers to be compromised by an outside attacker because of its visibility and availability. If your web server is located within the firewall, then the attacker will have an ideal foothold for launching further attacks against your organization. This is a serious concern, because organizations that use firewalls often have weaker internal security than those that rely on strong internal security measures to prevent attacks and unauthorized use.
If your web server is repeatedly attacked from a particular host on the Internet, a short-term fix is to locate an additional router between your outside network connection and your web server so that these “attack packets” are dropped rather than passed through to your web server. A longer-term fix is to contact the attacker’s Internet service provider or notify a law enforcement agency.
Get Web Security and Commerce now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.