Testing the Handler
We’re going to do something a little different in this chapter. We’re going to test the handler we have just created. Why? Because it doesn’t work. Oh, we wrote it correctly; it just doesn’t work. And it’s not even our fault. Let’s take a look.
First, restart the shell. Now, move a folder somewhere on your system. You should see the dialog shown in Figure 9.1.
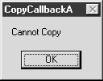
Figure 9-1. The first attempt to move a folder
Everything looks good so far. “So what’s the problem?” you ask. Move the folder back to its original location, and then you’ll see.
Boom!
As you can see from Figure 9.2, the component crashes the shell the second time around.
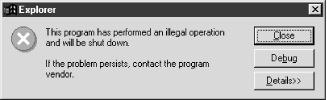
Figure 9-2. A second, unsuccessful attempt to move a folder
If you have compiled RadEx with symbolic debugging info and you have Visual C++ installed on your machine, Windows will give you the option to debug the component. Looking at a bunch of assembly code won’t really do the average programmer any good, but the debugger does give you the option to look at the call stack. The call stack will show you where the crash occurred and what functions were called before it. Typically, when the copy hook handler we have created crashes, the call stack looks something like this:
0045fe24( ) SHELL32! 7fd1f771( ) SHELL32! 7fd1cdd9( ) SHELL32! 7fd1de1a( ) ...
Get VB Shell Programming now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

