User-Centric Trust
In the model typically referred to as user-centric trust, each user is directly and totally responsible for deciding which certificates to rely on and which to reject. This decision may be influenced by a number of factors, although the initial set of trusted keys often includes those of friends, family, or colleagues a given user knows personally. See Figure 9.4.
Figure 9.4. User-centric trust model.
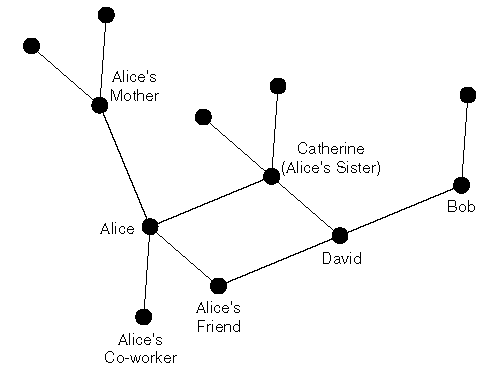
User-centric trust is probably best illustrated by the well-known security software program Pretty Good Privacy (PGP) [Zim95, Gar95], particularly in its more recent incarnations (version 5.0 and later). In PGP, a user builds ...
Get Understanding Public-Key Infrastructure: Concepts, Standards, and Deployment Considerations now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

