SSH Access to a Database
Two types of remote database access scenarios are briefly discussed in this section. In the first scenario, the user directly logs in to the database server through Secure Shell (SSH) (to take advantage of the security benefits of encrypted sessions) and then starts a program on the server to access the database. In this case, shown in Figure 29.4, the database client is running on the database server itself.
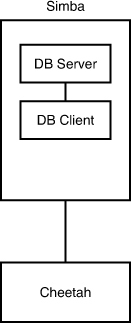
FIGURE 29.4 The user logs in to the database server located on host simba from the workstation (host cheetah). The database client is running on simba.
In the other scenario, shown in Figure 29.5, the user logs in ...
Get Ubuntu Unleashed 2014 Edition: Covering 13.10 and 14.04,Ninth Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

