3.1. The Yahalom protocol
Recall the Yahalom protocol:
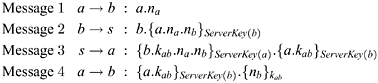
In itself, this description does not state what the protocol aims to achieve. The expectation that it provides authentication of each of its participants to the other must be made explicit, as must the requirement that the key kab distributed to the participants must be secret. The property that the nonce nb should be secret at the end of the protocol can also be expressed. This may or may not be a requirement of the protocol, depending on its intended use.
The CSP description of the protocol was given in Chapter 2. The individual runs of the initiator and responder are:
The Yahalom protocol ...
Get The Modelling and Analysis of Security Protocols: the CSP Approach now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

