Attack Fallout Traffic Analysis
The other application of black-hole monitoring relies on observing traffic that was never aimed at us in the first place, but which is merely a side effect of other activity.
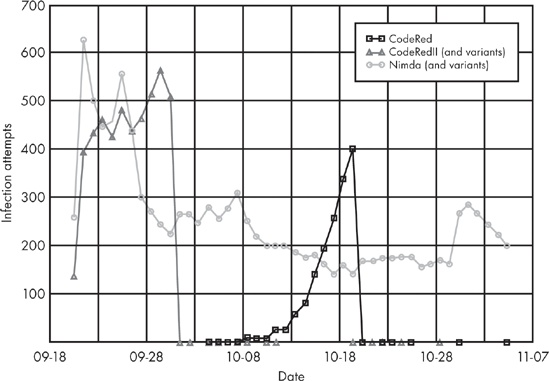
Figure 18-4. Worm persistence over time. Note that there is no trivial spike-falloff pattern for CodeRed and that the model behaves like a biological population model.
Here we can see how a number of common reconnaissance and attack schemes use address spoofing to conceal an attacker’s identity. The assumption is that an administrator will have difficulty differentiating decoy traffic from bogus addresses from the attacker’s actual probes. Although ...
Get Silence on the Wire now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

