Choosing Event Sources for Blanco Wireless
Figure 5-6 shows the configuration of event source collection for Blanco’s security monitoring. Notice that Blanco has configured NetFlow, NIDS, syslog, application logs, and database audit logs to detect policy violations affecting its selected monitoring targets.
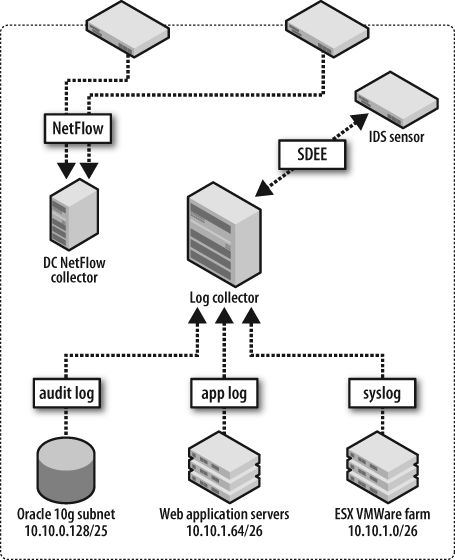
Figure 5-6. Blanco’s selected security event sources
To monitor the targets selected in Chapter 4, Blanco has enabled NetFlow export from its data center routers, storing the flow data in a NetFlow collector system. Blanco’s security team will use this data to identify connections sourced from critical systems toward external systems, and to identify large volume copies from database systems.
Blanco’s Unix servers are configured to send messages to a syslog
collection server. The security team will monitor these messages for
direct privileged logins and privilege escalation via sudo. The servers are also configured to log and
relay messages recording stops and starts for the web server, SSH, and
database processes.
Blanco’s NIDS is configured to monitor for known attacks against the Oracle suite. The security team has created custom signatures to identify:
Unencrypted transmission of Social Security numbers (a policy violation)
The
describecommand issued against any production database (an indication of database enumeration by someone unfamiliar with the schema)
Blanco’s database administrators ...
Get Security Monitoring now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

