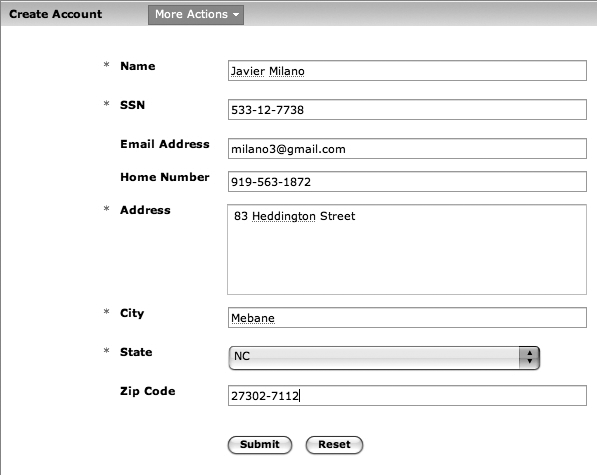
Like most wireless phone carriers, Blanco collects Social Security numbers from customers when setting up their accounts, illustrated in Figure 4-8. Blanco uses this information to request and report credit information from one of the large credit reporting services. As described in Chapter 2, Blanco has formed policies designed to protect such information and comply with government regulation.
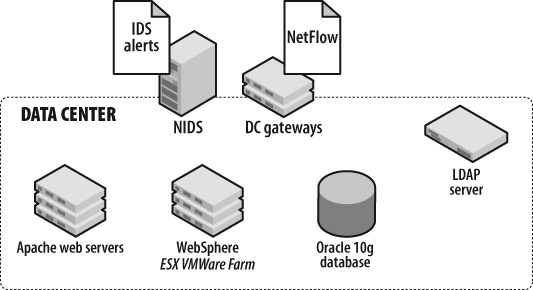
Blanco’s account management system, shown in Figure 4-9, is composed of a common, three-tier architecture:
Apache web servers running on three load-balanced Red Hat Enterprise Linux (RHEL) servers
An IBM WebSphere Application Server running on a VMware ESX server farm
An Oracle database (11g), clustered and distributed across two RHEL servers
An OpenLDAP server running on one RHEL server
Data center gateways (two Cisco IOS 7200 routers)
A NIDS (one Sourcefire Snort server)
Although not pictured in Figure 4-9, load-balancing intelligence is built into the network, reducing the need for separate, specialized equipment.
In Chapter 5, we’ll discuss the best event feeds to use for monitoring our target system. Our task for now, however, is to identify each component in the solution. Considering the two policies articulated in the section Introducing Blanco Wireless, we must configure monitoring for the Data Protection Policy and the Server Security Policy.
To effectively monitor compliance with the Data Protection Policy, we must monitor the database for plain-text PII in storage, the network gear providing access to the database, and the database configuration, to make sure the database complies with our hardening specs. Our Data Protection Policy requires us to do the following:
Audit data stored in the database via scheduled queries, or by monitoring the audit log of the database itself to ensure that the data is encrypted properly.
Monitor network traffic, which is satisfied by NIDSs deployed at the data center gateway.
Ensure that the database configuration is hardened. This will require a routine audit against the database, using a programmatic, scheduled vulnerability testing tool such as Nessus.
The Server Security Policy will require monitoring of every deployed server in our solution, including web servers, application servers, and database servers. We must also monitor the LDAP server to track account access, and must access network feeds (using NetFlow) to monitor traffic accessing the Internet from these servers.
Get Security Monitoring now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.