How Does Secure Email Work?
Like the Kerberos authentication protocol, which you learned about in Chapter 7, secure email uses cryptography to validate the sender’s identify (in the case of digitally signed messages) or to protect the message’s content (in the case of encrypted messages).
Digitally Signed Messages
Figure A-1 illustrates how a user can send a digitally signed message using email software such as Microsoft Outlook.
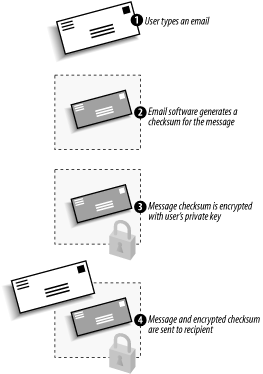
Figure A-1. Sending a digitally signed message
Here’s how it works:
The user types a regular email and tells Outlook to digitally sign the message.
Outlook calculates a checksum on the message. The checksum is the result of a mathematical hash algorithm and is different for every message. Changing a single character in the email would change the resulting checksum. (Remember that we discussed hash algorithms in Chapter 2.)
Outlook retrieves the user’s private encryption key from local storage and uses it to encrypt the checksum. The checksum is now a digital signature.
Both the unencrypted message and the signature are sent to the recipient.
Tip
Digital signatures do not prevent others from reading the text of the message. The message is sent in clear text; only the signature uses encryption. This encrypted signature is easily decrypted by anyone, as we will see.
The recipient must perform a somewhat more complex process to validate the digital signature, as illustrated ...
Get Securing Windows Server 2003 now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

