Building and maintaining a secure site on the Internet includes many more tasks than simply installing your operating system, however securely you may do so. Overall security is a combination of secure software and careful human planning and administration. You will need to be concerned with all of the following tasks:
- Planning
Securing an Internet site must be a carefully planned and coordinated process. It’s not just a matter of clicking on screens and working it out as you go. Figure out the goals and tactics ahead of time, and then implement security, step-by-step. It’s also important to understand that you need one encompassing plan that includes all aspects of the process, rather than several small and uncoordinated planning efforts.
- Policies
In order to achieve a high level of security, you need policies that define the main aspects of running an Internet site. This is not a book on policies, but keep in mind that before you start building a secure system, you need to have the appropriate policies in place. Start by reading the Site Security Handbook (RFC 2196); it’s an excellent introduction to this topic.
- Access control
Access control protects systems from unauthorized use; there are several different types:
- Physical access control
Physical access control[8] is often overlooked, but it’s an extremely important outer level of protection. Large organizations often have big computer rooms that are both bomb-proof and earthquake-proof, which is good. In many cases, however, pretty much everyone in the organization has access to these rooms, which makes it possible for anyone in the building to sabotage operations.
- System access control
Only the people involved in the daily operation of your systems should have access to these systems. Those who are granted access should have only the amount of privilege required to do their jobs. For example, not everyone needs to be a member of the Administrator group.
- Network access control
Network access to your systems needs to be restricted by a firewall system. A firewall system consists of a number of components that act in concert to enforce your network access policy; it’s typically not just one single gateway with firewall software installed. The perimeter network (discussed later in this chapter) is a type of firewall system.
- Operation
Once your system is up and running, you need to manage its operation in a careful and secure manner. System management includes:
- Auditing
Watch your systems carefully. Set up an audit policy that keeps you informed of any access policy violations. Chapter 6, deals with the different aspects of setting up auditing on a Windows NT/2000 bastion host.
- Backups
Make frequent backups. Always back up before and after changing the configuration of your systems. The flip side of backup is restore; you must attempt to restore your system from backups at regular intervals to make sure you’ll be able to do so if there is a disaster. Chapter 5, serves as an introduction to backing up and restoring bastion hosts.
- Log management
Collect logs in real time on a separate secured logging host and carefully review this information. Chapter 6 suggests a strategy using syslog as a transport mechanism for log collection.
- Peer reviews
Ask your colleagues or a third party to review your work periodically. See Chapter 7, for details.
- Encryption
Use encryption to secure communication and sensitive data stored on disk. You will find references to various types of encryption methods and algorithms throughout this book. Section 1.5 later in this chapter provides a brief introduction.
It’s important to understand that site security is a very big and complex subject and that this book’s focus on the practical aspects of building and managing secure bastion hosts based on Windows NT/2000 is a very narrow aspect of site security.
Microsoft’s success in the network operating system market is largely because its products are so easy to use. The Windows server version has the familiar user interface that almost all office workers use every day. It’s easy to get started, and you don’t need in-depth knowledge of the operating system to install a Windows NT/2000 server. Most components are configured and started automatically, just as they are in the consumer Windows 95/Windows 98 operating system. These characteristics are attractive for an internal file and print server that isn’t exposed to direct attack. However, you want something quite different for an external web server that serves the organization’s customers and partners over the Internet. A system exposed in this way should provide a minimum of services and needs to be properly configured to ensure a higher level of security. As I mentioned earlier in this chapter, a system configured in this manner is referred to as a bastion host.
Basically, a bastion host is a computer system that is a critical component in a network security system, and one that is exposed to attack. Examples of bastion hosts are firewall gateways, web servers, FTP servers, and Domain Name Service (DNS) servers. Because bastion hosts are so important—and so vulnerable—such systems must be highly fortified. You must pay special attention to fortifying (i.e., establishing the maximum possible security for) the bastion host during both initial construction and ongoing operation.
Why are such systems called bastion hosts? The American Heritage Dictionary defines a bastion as:
A projecting part of a rampart or other fortification.
A well-fortified position or area.
Something regarded as a defensive stronghold.
Marcus J. Ranum is generally credited with applying the term bastion to hosts that are exposed to attack, and with the popularization of the term in the firewall community. In “Thinking About Firewalls V2.0: Beyond Perimeter Security”[9] he wrote:
Bastions are the highly fortified parts of a medieval castle; points that overlook critical areas of defense, usually having stronger walls, room for extra troops, and the occasional useful tub of boiling hot oil for discouraging attackers. A bastion host is a system identified by the firewall administrator as a critical strong point in the network’s security. Generally, bastion hosts will have some degree of extra attention paid to their security, may undergo regular audits, and may have modified software.
Bastion hosts are not general-purpose computing resources. They differ in both their intent and their specific configuration. The process of configuring or constructing a bastion host is often referred to as hardening.
The effectiveness of a specific bastion host configuration can usually be judged by answering two questions:
How does the bastion host protect itself from attack?
How does the bastion host protect the network behind it from attack?
Chapter 2, and Chapter 3, provide detailed instructions for building a bastion host, using Windows NT and Windows 2000 respectively.
Exercise extreme caution when installing software on bastion hosts. Very few software products have been designed and tested to run safely on these exposed systems. For a thorough treatment of bastion hosts, and on firewalls in general, I recommend reading Building Internet Firewalls, Second Edition.
No matter how carefully you configure your bastion host to withstand direct attacks, you can’t be entirely confident about its security. Most software code has bugs in it, and therefore all systems potentially have undiscovered security vulnerabilities. For this reason, it’s important to provide extra layers of security for systems that are as exposed and as vulnerable as bastion hosts.
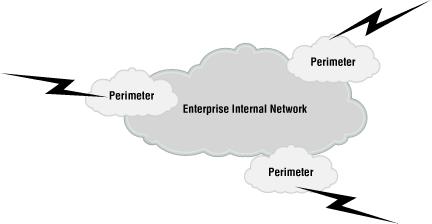
A common way to protect exposed servers on the Internet is to implement some kind of network-based access control mechanism that serves as extra protection for the bastion hosts. One such very effective mechanism is provided by a perimeter network. A perimeter network is a network that connects your private internal network to the public Internet or another untrusted network. This makes the perimeter network very important from a security standpoint. The purpose of this network is to serve as a single point of access control. All components in a perimeter must act in concert to implement a site’s firewall policy. In other words, the perimeter network is a firewall system.
The perimeter network is a key part of the architecture of many current Internet sites. The reasons are partly historical. When the Internet took off commercially, many companies wanted to get on the Net to do business. The first step was often simply to publish product information on a web server. These web servers typically contained only static information, and thus didn’t need to be connected to the internal network. With the advent of e-commerce, such web servers had to be connected in some way both to the clients on the Internet and to the legacy systems on the internal network — for example, to process orders and check the availability of products.
Many companies now faced the requirement to connect their internal networks to the Internet—and to the accompanying security risks. Since the Internet could not be trusted for obvious reasons, there was an increasing need for company-controlled networks that could act as secured perimeters.
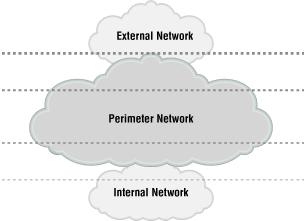
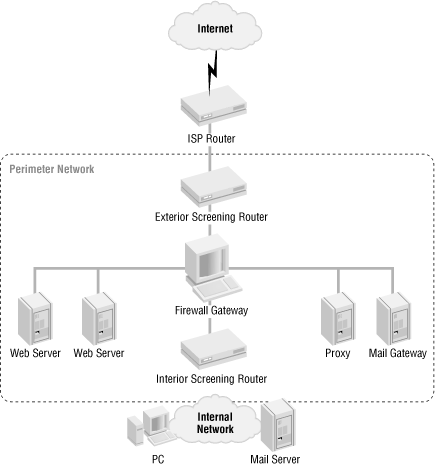
A perimeter network is an untrusted part of an enterprise network that resides on the outskirts of the private network. The perimeter network is often also referred to as the demilitarized zone , or DMZ, named after the region separating North Korea and South Korea. An example of a perimeter network is where the Internet connection and the web servers are located. A company might have several perimeter networks, as illustrated in Figure 1.2.
All external communication from the internal network has to pass the perimeter before it can reach an external host, and no communication is allowed directly from an external network to the internal network.
A good approach to building the perimeter network is to build it in compartments, so that the perimeter is able to protect itself and the internal network even if one compartment is compromised. This compartmentalization is illustrated in Figure 1.3.
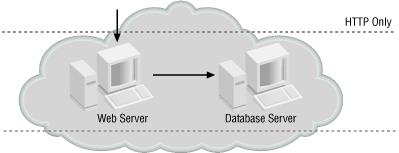
Because each compartment has access control mechanisms, the farther in from the external network a host is placed, the better it is protected. It’s good security practice to block as much traffic as possible in each compartment layer—I recommend that you take a default-deny stance regarding network traffic. With a default-deny stance, everything that isn’t explicitly allowed is denied, in contrast to a default-allow stance, where everything that isn’t explicitly denied is allowed. Consider the example in Figure 1.4.
In this example, if the web server is compromised, it’s easy for an intruder to attack any service provided by the database server. This is because there is no network access control between these two servers.
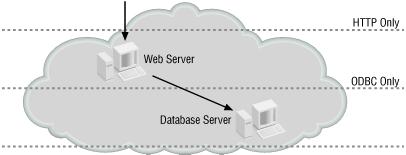
On the other hand, in the topology shown in Figure 1.5, if the web server is compromised, the access control layer between the compartments will block unneeded traffic to the database system. As a result, the intruder may be able to attack the database process on the server, but not be able to attack anything else.
It takes a number of different components to build a perimeter network, and some architectures are quite complex. This section does not attempt to describe all of the issues or possible combinations. It simply introduces the components and explains how they interact so you will have enough background to be able to understand subsequent chapters.
- Routers
Routers are the traffic police of the network. They decide what route a datagram should take at each router or “network intersection.” Like the police, routers can also choose to stop certain types of traffic. Traffic is controlled by rules called router Access Control Lists (ACLs). Example 1.1 shows a router ACL for a Cisco router.
Example 1-1. Cisco IOS Router ACL Example
ip access-list extended example_access_list permit tcp any 192.168.1.0 0.0.0.255 eq http permit icmp any any deny ip any any log
A Cisco IOS ACL is applied from top to bottom. An incoming datagram is tested against each line in the ACL. This example allows HTTP from anywhere to the 192.168.1/24 network. It also allows any type of ICMP anywhere. All other datagrams[10] are blocked and logged.
Using router ACLs in this manner provides us with a useful network access control mechanism in the perimeter. A router that implements access control in this manner is generally referred to as a screening router .
- Firewall gateways
Certain components in the perimeter typically have firewall software installed, and these machines are referred to as firewall gateways.
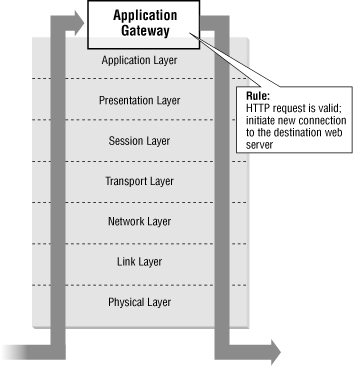
There are two common techniques that a firewall gateway can use. One method, shown in Figure 1.6, is to act as an application-level gateway; the gateway serves as a middleman that intercepts traffic at the application level, and it initiates a new connection to the target system on behalf of the client. Examples of application-level protocols are File Transfer Protocol (FTP), HyperText Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), and Post Office Protocol (POP).
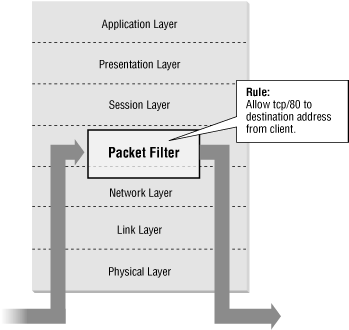
The other technique, illustrated in Figure 1.7, is to inspect the traffic on the Internet Protocol (IP) level. This is called packet filtering . A more sophisticated form of packet filtering, called stateful inspection , is used by products such as Checkpoint’s Firewall-1. A state-aware firewall gateway keeps track of the state of the connections that are going through it. If an outgoing HTTP request from a client is allowed through the gateway, the response to that request also has to be allowed through. The firewall software adds a temporary rule in its rulebase to allow the response from the destination web server to the client. The firewall gateway also understands some types of application data (HTTP, SMTP, FTP, etc.) in the IP datagrams, and for this reason, it may be able to make better security decisions than a screening router can.
In theory, an application-level proxy can make more sophisticated decisions, but it’s usually slower than inspecting the IP datagrams. As “inspection” technology gets more sophisticated (it’s now becoming possible to keep track of the state of many application-level protocols), the gap between the two approaches lessens. Many firewall products provide both application-level proxies and IP-level inspection or filtering. These products are referred to as hybrids.
- Bastion hosts
The bastion hosts are the application servers in the perimeter. A bastion host usually runs one specific piece of software, such as a mail gateway or some web server software. A bastion host has no unnecessary services running, and it is installed and configured in a highly secured manner, as described in Chapter 2 and Chapter 3.
- Switches and hubs
As with any other network, you need switches or hubs to build the network infrastructure in the perimeter. A network segment that uses a hub is a shared media, where all traffic is visible from all network stations (hosts). On the other hand, a switch connects the sender directly to the receiver for every Ethernet packet. This provides improved performance for unicast (one-to-one) traffic, but also some additional security. If one of the hosts on a network segment is compromised, an intruder may be able to install a network sniffer to spy on traffic on that segment to get information. However, if a switch is used, the intruder may not be able to see the traffic between other hosts.
I recommend that you use “dumb” switches and hubs without management software if possible. If the switch or hub device has its own IP stack, it may be vulnerable to attacks, and for this reason, it will have to be secured in the same manner as your bastion hosts.
The best way to describe how all the components fit together is to present an example perimeter network design. The example network I describe in this section is very general and simplified; don’t use it as a ready-to-run implementation blueprint.
What are the objectives of this design?
A design always has to meet some core objectives. These are usually determined by specific business requirements. Let’s assume that our example company has the following needs:
It must allow access to the web servers from the Internet.
It must accept incoming mail.
It must allow outbound web and FTP from the internal network.
It must allow outgoing mail.
The example company must solve these business objectives with regard to two key network security needs:
No direct traffic can be allowed between the Internet and the internal network.
If one component in the perimeter is compromised, it should not result in a compromise of the entire perimeter or the internal network.
What’s a possible solution to these problems and objectives?
The solution shown in Figure 1.8 meets all the objectives of this example and protects the perimeter both from external and internal threats. The solution implements a perimeter network with the web servers, a firewall gateway, a mail gateway, and an HTTP proxy server.
In this example, the following services are allowed:
Only inbound HTTP to the web servers and inbound SMTP to the mail gateway are allowed from the Internet.
The proxy server and mail gateway are allowed to do DNS queries (udp/53).
The proxy is allowed outbound HTTP, HTTPS, and FTP.
The mail gateway is allowed to send mail (SMTP) to the Internet and to relay incoming mail to the internal mail server.
The internal mail server is allowed to relay outgoing mail to the mail gateway.
The internal network is allowed to use the proxy server in the perimeter.
The screening routers protect the perimeter from the Internet and the internal network from the perimeter in case there is a problem with the firewall gateway. You’ll notice that no direct traffic is allowed between the internal network and the Internet and vice versa.
The proxy and mail servers are placed on a different network from the web servers; doing so separates outgoing web surfing from published web services. In the future, the company might consider a separate Internet connection for outgoing web traffic to guarantee bandwidth to its public web servers.
This design has four separate security zones:
Two zones between the firewall and the screening routers
One zone for the web servers
One zone for the mail gateway and proxy server
As a result, the perimeter is well compartmentalized; if one security zone is compromised, the others remain intact. Note that if the firewall gateway is compromised, multiple security zones are also compromised. However, the interior screening router still protects the internal network.
All the components in the perimeter must be hardened to a very high
level. This implies removing all unneeded or unsecure services that
are provided by default. An easy thing to do is to list the active
network services with a command (netstat
-an on most operating systems), and to scan and
probe the host for available services to identify which services you
need and which ones you can turn off
or
remove.
[8] Practical Unix and Internet Security, Second Edition, by Simson Garfinkel and Gene Spafford (O’Reilly, 1996) has an excellent chapter on physical security. You might consider checking it out even if you don’t need the Unix details.
[9] Available at http://pubweb.nfr.net/~mjr/pubs/think/index.htm.
[10] Non-first TCP fragments are permitted. See RFC 1858, “Security Considerations for IP Fragment Filtering,” for details.
Get Securing Windows NT/2000 Servers for the Internet now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.