Chapter 5
Abusing the Hypervisor
Vision is the art of seeing things invisible to others.
—Jonathan Swift
This chapter reviews the many ways in which the central element of virtualization—the hypervisor—is at risk of compromise and manipulation. Figure 5.1 illustrates how Microsoft's Hyper-V sits on hardware. The various paths and layers of separation are a tempting challenge to attackers.
Figure 5.1 Hyper-V architecture
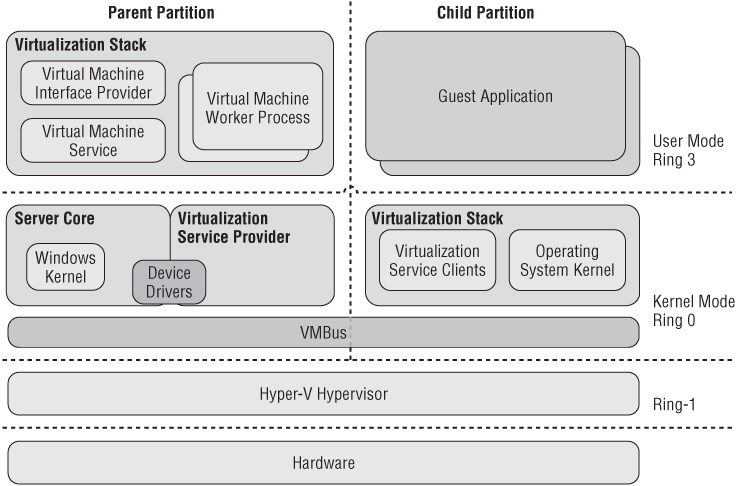
The partitions are only logical units meant to isolate operating systems. An initial setup of the hypervisor would have a parent partition running Microsoft's Windows Server 2008, which then creates the child partitions to isolate guest operating systems. Direct access to hardware is designed to be available only through the parent partition. Children are given access via a virtualized interface provided by the parent called the VMBus. NIST Special Publication 800-125 supports this model of isolation but gives it a less-than-stellar endorsement.1
NIST notes that hypervisors can, in theory, support logical isolation of different virtual machines in a manner which is almost equivalent to physically distinct hosts. They also warn that “physical separation” may have “stronger security and improved performance” when compared to logical isolation. An example given is a copy/paste buffer resource on the host system, which may be exposed to more than one guest system.
Get Securing the Virtual Environment: How to Defend the Enterprise Against Attack, Included DVD now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

