Costs of Threats and Countermeasures
Once you’ve identified the costs of implementing controls, your next step is to estimate the costs of the threats you face based on your social media activities. In Chapter 4, we walked you through an assessment process for identifying potential threats. If you know those potential threats, you can utilize Tables 9-2 and 9-3 to analyze the potential costs of those threats and the countermeasures you put in place to counteract the threats. (See the Ponemon study for costs, http://www.ponemon.org/local/upload/fckjail/generalcontent/18/file/2010%20Global%20CODB.pdf.)
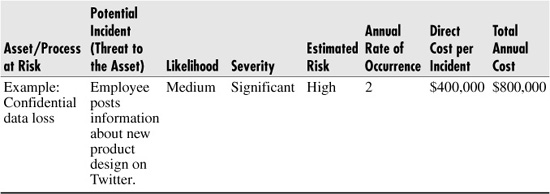
Table 9-2 Costs of Threats
Table 9-3 Costs ...
Get Securing the Clicks Network Security in the Age of Social Media now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

