5.3. Digital Signatures
PK encryption can be used for digitally signing an electronic document in a way that allows for later validation for authenticity [5]. We explain here, with the help of Fig. 5.3, how digital signatures work.
Figure 5.3. Digital Signatures.
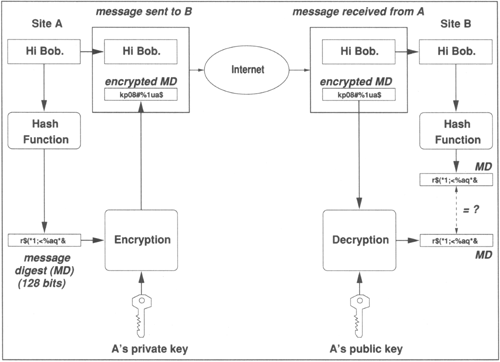
Suppose that A wants to send a message Msg to B. The following steps are followed by A before sending the message.
1. |
A generates a fixed size string, called the message digest (MD), by applying a one-way hash function h to the message Msg. So MD = h (Msg). For a hash function to be useful for digital signatures, it must have the following properties:
|
Get Scaling for E-Business now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

