6Policing and Shaping
The first part of this book presented the policer and shaper tools as black boxes and gave a high-level view of their functionalities. This chapter goes one step further and takes a closer look at the fundamental mechanics of these tools.
Policers are implemented using the concept of a token bucket, while shapers use leaky buckets. These are the two key concepts on which this chapter focuses. We explain both and compare the two in terms of applicability and differences regarding how to use them to deal with traffic burstiness and excess traffic.
6.1 Token Buckets
When viewed as a black box, the policer operation is pretty straightforward: at the ingress is a traffic flow with a certain bandwidth value and at the egress is the “same” traffic flow that is now enforced to conform to the bandwidth value defined by the policer. One result is that “excess traffic” is discarded, a behavior also commonly called rate limiting. This policer operation is illustrated in Figure 6.1.
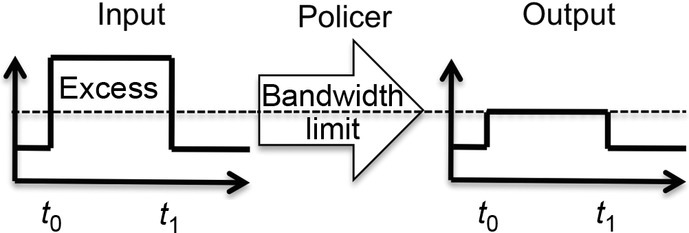
Figure 6.1 High-level view of the policing operation
In Figure 6.1, the policer limits the input traffic to a certain bandwidth limit (represented as a dotted line). During the time interval between t0 and t1, the input traffic exceeds the bandwidth limit value, which results in the excess traffic being discarded by the policer. While it is not mandatory, the usual action taken regarding ...
Get QOS-Enabled Networks, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

