Identifying the target
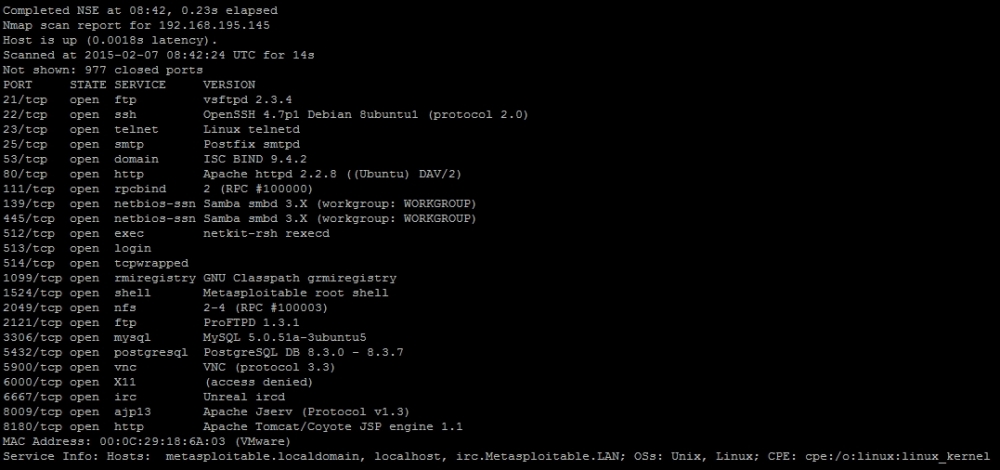
We are going to use Metasploitable as an example here, because it will allow you to test these concepts in a safe and legal environment. To start with, let us do a simple nmap scan of the system with a service detection. The following command highlights the specific arguments and options, which does SYN scan looking for the well-known ports on a system.
nmap -sS -vvv -Pn -sV<targetIP>
As you can see from the results, the host is identified as Metasploitable and a number of ports are open to include Simple Mail Transfer Protocol (SMTP) at port 25.
Get Python: Penetration Testing for Developers now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

