Step 6: Make Signed Requests for Privileged User Data
The last step of the hybrid auth process involves the relaying party taking the access token object generated from the token exchange in step 5 and making signed requests to the provider in order to obtain privileged resources from a user, such as his profile information, friend data, or activity stream updates.
The process looks similar to Figure 12-4.
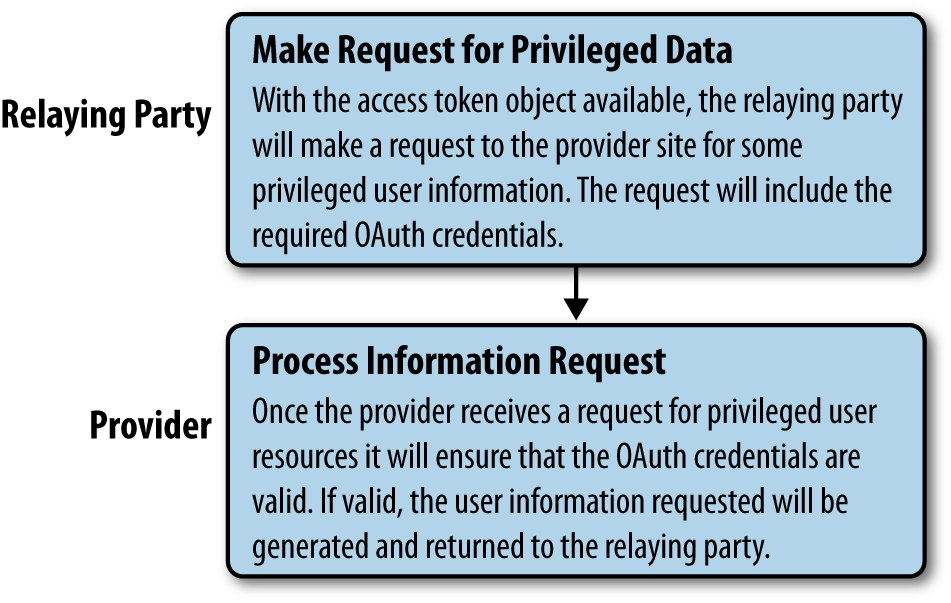
Figure 12-4. Hybrid auth, step 6: Relaying party makes privileged user data requests through the provider
The relaying party will generate a signed HTTP request to a URI endpoint on the provider site that is set up to return the resources that we are looking for. This request will include the access token parameters from the object we generate.
Warning
Different providers accept the OAuth access token parameters in different ways. Some may require that data be sent via the HTTP headers, while others may accept the data in the POST body. You should check with the provider you are working with to ensure that you are passing the token information through in the way it expects and requires.
The provider will receive that request, validate the access token, and issue the requested information as a response object back to the relaying party, provided that the OAuth scopes associated with the request are sufficient for accessing the requested data.
Get Programming Social Applications now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

