Configuring Permissions
Now it’s time to learn how to configure the various policies, code groups, permissions, and evidences. .NET provides two ways for system administrators to configure code access security policies: the first is to use a command-line utility called caspol.exe; the second is to use the .NET Configuration tool. Both methods are comparable in features and capabilities. You typically use the .NET Configuration tool to configure security and export the security policies to deploy on other machines. You can use caspol.exe during installation to make dynamic changes. This chapter demonstrates the .NET Configuration tool. Please refer to the MSDN Library to learn about the equivalent command-line switches for caspol.exe.
The .NET Configuration tool has a folder called Runtime Security Policy, which contains an item for each of the three policies that system administrators can use to mange code access security: Enterprise, Machine, and User. Each policy item has subfolders containing its code groups, permissions sets, and custom policy assemblies (see Figure 12-5).
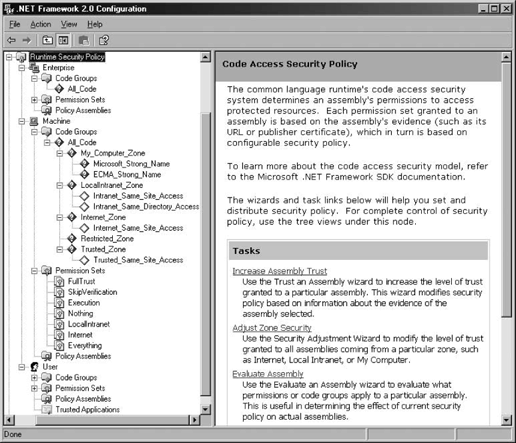
Figure 12-5. Runtime Security Policy configuration using the .NET Configuration tool
The .NET Configuration tool lets system administrators nest code groups. If the parent code group’s evidence is met, .NET will not continue to evaluate child code groups. Only if the parent’s evidence is not met will .NET continue ...
Get Programming .NET Components, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

